If your device is semi bricked and entered the usb pid 0x900E, there are several options Install and configure a Python development environment. As mentioned above, modern EDL programmers implement the Qualcomm Firehose protocol. You saved my phone. which [5][unreliable source?] Other devices, such as the OnePlus family, test a hardware key combination upon boot to achieve a similar behavior. As one can see, the relevant tag that instructs the programmer to flash a new image is program.  The merit of our research is as follows: * QPSIIR-909, ALEPH-2017029, CVE-2017-13174, CVE-2017-5947. As for remediation, vendors with leaked programmers should use Qualcomms Anti-Rollback mechanism, if applicable, in order to prevent them from being loaded by the Boot ROM (PBL), The problem is caused by customizations from OEMsOur Boot ROM supports anti-rollback mechanism for the firehose image., Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6's Secure Boot, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting, Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals, Obtain and reverse-engineer the PBL of various Qualcomm-based chipsets (, Obtain the RPM & Modem PBLs of Nexus 6P (, Manifest an end-to-end attack against our Nokia 6 device running Snapdragon 425 (. 4. or from here, Make a subdirectory "newstuff", copy your edl loaders to this subdirectory, or sniff existing edl tools using Totalphase Beagle 480, set filter to filter({'inputs': False, 'usb3': False, 'chirps': False, 'dev': 26, 'usb2resets': False, 'sofs': False, 'ep': 1}), export to binary file as "sniffeddata.bin" and then use beagle_to_loader sniffeddata.bin. JavaScript is disabled. To flash the firmware, the tool communicates with supported devices via EDL. There was a problem preparing your codespace, please try again. Format of the Course. This mobile technology related article is a stub. Webedl peekqword 0x200000-> To display a qword (8-bytes) at offset 0x200000 from memory; edl pokeqword 0x200000 0x400000-> To write the q-word value 0x400000 to offset Topics include: Predictive analytics is the process of using data analytics to make predictions about the future. We dive into data analysis, visualization, modeling and programming by way of hands-on exercises and plentiful in-lab practice. In fastboot mode Go to the extracted files and double click on the flashall_aft file and sit back and wait until it finishes. Themes of data analysis, visualization, modeling, and programming are explored throughout the course. Please No prior programming experience or knowledge of MATLAB is assumed. Course: Introduction au Machine Learning avec MATLAB. If nothing happens, download Xcode and try again. Register a free account today to become a member! You must log in or register to reply here. In the third part of the training, participants learn how to streamline their work by automating their data processing and report generation. The course will show you how to use the program in many practical examples. The cable also works on hard-bricked devices to boot them into EDL mode. 800 Corporate Drive, Suite 301. Qualcomm implemented motherboards, with the presence of EDL, can be booted to EDL via the use of a EDL Deep Flash Cable. With the use of the cable, in most devices and cases, it will not be necessary the use of test points. It soon loads the digitally-signed SBL to internal memory (imem), and verifies its authenticity. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. It's usually included with MiFlash at XiaoMiFlash\Source\ThirdParty\Qualcomm\fh_loader\lsusb.exe (In fact, this is what MiFlash itself uses to identify the virtual COM port.) Assessments will be conducted throughout the course to gauge progress. Log in Register Home Forums Are you sure you want to create this branch? as well as how to apply MATLAB's packages such as Financial Toolbox to perform mathematical and statistical analysis of financial data. During this process, EDL implements the Firehose/Sahara protocol and acts as a Secondary Bootloader to accept commands for flashing. The course is intended for beginner users and those looking for a review. This instructor-led, live training in Virginia (online or onsite) is aimed at Matlab users who wish to explore and or transition to Python for data analytics and visualization. Later, the PBL will actually skip the SBL image loading, and go into EDL mode. Stafford, VA 22554. For a better experience, please enable JavaScript in your browser before proceeding. Virginia onsite live MATLAB trainings can be carried out locally on customer premises or in NobleProg corporate training centers. User: user, Password:user (based on Ubuntu 22.04 LTS), You should get these automatically if you do a git submodule update --init --recursive 3. Objective: This training is meant for software Engineers who are working with MBD technology, the training will cover Modelling techniques for Automotive systems, Automotive standards ,Auto-code generation and Model test harness building and verification Audience: Software developper for automotive supplier. Is there a way to force shut down so i can charge it?
The merit of our research is as follows: * QPSIIR-909, ALEPH-2017029, CVE-2017-13174, CVE-2017-5947. As for remediation, vendors with leaked programmers should use Qualcomms Anti-Rollback mechanism, if applicable, in order to prevent them from being loaded by the Boot ROM (PBL), The problem is caused by customizations from OEMsOur Boot ROM supports anti-rollback mechanism for the firehose image., Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6's Secure Boot, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting, Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals, Obtain and reverse-engineer the PBL of various Qualcomm-based chipsets (, Obtain the RPM & Modem PBLs of Nexus 6P (, Manifest an end-to-end attack against our Nokia 6 device running Snapdragon 425 (. 4. or from here, Make a subdirectory "newstuff", copy your edl loaders to this subdirectory, or sniff existing edl tools using Totalphase Beagle 480, set filter to filter({'inputs': False, 'usb3': False, 'chirps': False, 'dev': 26, 'usb2resets': False, 'sofs': False, 'ep': 1}), export to binary file as "sniffeddata.bin" and then use beagle_to_loader sniffeddata.bin. JavaScript is disabled. To flash the firmware, the tool communicates with supported devices via EDL. There was a problem preparing your codespace, please try again. Format of the Course. This mobile technology related article is a stub. Webedl peekqword 0x200000-> To display a qword (8-bytes) at offset 0x200000 from memory; edl pokeqword 0x200000 0x400000-> To write the q-word value 0x400000 to offset Topics include: Predictive analytics is the process of using data analytics to make predictions about the future. We dive into data analysis, visualization, modeling and programming by way of hands-on exercises and plentiful in-lab practice. In fastboot mode Go to the extracted files and double click on the flashall_aft file and sit back and wait until it finishes. Themes of data analysis, visualization, modeling, and programming are explored throughout the course. Please No prior programming experience or knowledge of MATLAB is assumed. Course: Introduction au Machine Learning avec MATLAB. If nothing happens, download Xcode and try again. Register a free account today to become a member! You must log in or register to reply here. In the third part of the training, participants learn how to streamline their work by automating their data processing and report generation. The course will show you how to use the program in many practical examples. The cable also works on hard-bricked devices to boot them into EDL mode. 800 Corporate Drive, Suite 301. Qualcomm implemented motherboards, with the presence of EDL, can be booted to EDL via the use of a EDL Deep Flash Cable. With the use of the cable, in most devices and cases, it will not be necessary the use of test points. It soon loads the digitally-signed SBL to internal memory (imem), and verifies its authenticity. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. It's usually included with MiFlash at XiaoMiFlash\Source\ThirdParty\Qualcomm\fh_loader\lsusb.exe (In fact, this is what MiFlash itself uses to identify the virtual COM port.) Assessments will be conducted throughout the course to gauge progress. Log in Register Home Forums Are you sure you want to create this branch? as well as how to apply MATLAB's packages such as Financial Toolbox to perform mathematical and statistical analysis of financial data. During this process, EDL implements the Firehose/Sahara protocol and acts as a Secondary Bootloader to accept commands for flashing. The course is intended for beginner users and those looking for a review. This instructor-led, live training in Virginia (online or onsite) is aimed at Matlab users who wish to explore and or transition to Python for data analytics and visualization. Later, the PBL will actually skip the SBL image loading, and go into EDL mode. Stafford, VA 22554. For a better experience, please enable JavaScript in your browser before proceeding. Virginia onsite live MATLAB trainings can be carried out locally on customer premises or in NobleProg corporate training centers. User: user, Password:user (based on Ubuntu 22.04 LTS), You should get these automatically if you do a git submodule update --init --recursive 3. Objective: This training is meant for software Engineers who are working with MBD technology, the training will cover Modelling techniques for Automotive systems, Automotive standards ,Auto-code generation and Model test harness building and verification Audience: Software developper for automotive supplier. Is there a way to force shut down so i can charge it?  The first part presents some internals of the PBL, EDL, Qualcomm Sahara and programmers, focusing on Firehose. There are no posts matching your filters. https://alephsecurity.com/2018/01/22/qualcomm-edl-1/, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting Software Engineer at BounceX The venue is located behind a complex of commercial buildings with the Bank of America just on the corner before the turn leading to the office. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. By the end of this training, participants will be able to: In this instructor-led, live training, participants will learn how to use Matlab to design, build, and visualize a convolutional neural network for image recognition. It contains the init binary, the first userspace process. The training recipients are beginners but also those who know the program and would like to systematize their knowledge and improve their skills. Some Linux distributions come with ModemManager, a tool for configuring Mobile Broadband. After extracting, you will be able to see the following files: Step 3: Now, Run the QFIL tool.
The first part presents some internals of the PBL, EDL, Qualcomm Sahara and programmers, focusing on Firehose. There are no posts matching your filters. https://alephsecurity.com/2018/01/22/qualcomm-edl-1/, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting Software Engineer at BounceX The venue is located behind a complex of commercial buildings with the Bank of America just on the corner before the turn leading to the office. * We describe the Qualcomm EDL (Firehose) and Sahara Protocols. By the end of this training, participants will be able to: In this instructor-led, live training, participants will learn how to use Matlab to design, build, and visualize a convolutional neural network for image recognition. It contains the init binary, the first userspace process. The training recipients are beginners but also those who know the program and would like to systematize their knowledge and improve their skills. Some Linux distributions come with ModemManager, a tool for configuring Mobile Broadband. After extracting, you will be able to see the following files: Step 3: Now, Run the QFIL tool.  You saved my phone. Learn more. MATLAB is a numerical computing environment and programming language developed by MathWorks. 6. If nothing happens, download GitHub Desktop and try again. Concretely, in the next chapters we will use and continue the research presented here, to develop: 73C51DE96B5F6F0EE44E40EEBC671322071BC00D705EEBDD7C60705A1AD11248, 74F3DE78AB5CD12EC2E77E35B8D96BD8597D6B00C2BA519C68BE72EA40E0EB79, D18EF172D0D45AACC294212A45FBA91D8A8431CC686B164C6F0E522D476735E9, 9B3184613D694EA24D3BEEBA6944FDB64196FEA7056C833D38D2EF683FD96E9B, 30758B3E0D2E47B19EBCAC1F0A66B545960784AD6D428A2FE3C70E3934C29C7A, 8D417EF2B7F102A17C2715710ABD76B16CBCE8A8FCEB9E9803733E731030176B, 02FFDAA49CF25F7FF287CAB82DA0E4F943CABF6E6A4BFE31C3198D1C2CFA1185, EEF93D29E4EDDA26CCE493B859E22161853439DE7B2151A47DAFE3068EE43ABE, A1B7EB81C61525D6819916847E02E9AE5031BF163D246895780BD0E3F786C7EE, 97EFF4D4111DD90523F6182E05650298B7AE803F0EC36F69A643C031399D8D13, C34EC1FDDFAC05D8F63EED3EE90C8E6983FE2B0E4B2837B30D8619A29633649C, 63A47E46A664CCD1244A36535D10CA0B97B50B510BD481252F786177197C3C44, 964B5C486B200AA6462733A682F9CEAD3EBFAD555CE2FF3622FEA8B279B006EE, 71C4F97535893BA7A3177320143AC94DB4C6584544C01B61860ACA80A477D4C9, CB06DECBE7B1C47D10C97AE815D4FB2A06D62983738D383ED69B25630C394DED, A27232BF1383BB765937AEA1EBDEE8079B8A453F3982B46F5E7096C373D18BB3, 3FDAF99FC506A42FCBC649B7B46D9BB8DD32AEABA4B56C920B45E93A4A7080EA, 48741756201674EB88C580DF1FDB06C7B823DC95B3FC89588A84A495E815FBD4, 8483423802d7f01bf1043365c855885b0eea193bf32ed25041a347bc80c32d6b, 5F1C47435A031331B7F6EC33E8F406EF42BAEF9A4E3C6D2F438A8B827DD00075, 5D45ECF8864DBBC741FB7874F878126E8F23EE9448A3EA1EDE8E16FE02F782C0, 1D4A7043A8A55A19F7E1C294D42872CD57A71B8F370E3D9551A796415E61B434, BF4E25AE6108D6F6C8D9218383BD85273993262EC0EBA088F6C58A04FC02903B, 3DB3B7FD2664D98FD16F432E8D8AD821A85B85BD37701422F563079CB64D084C, ADEB0034FC38C99C8401DCDBA9008EE5A8525BB66F1FC031EE8F4EFC22C5A1DF, 67A7EA77C23FDD1046ECCE7628BFD5975E9949F66ADDD55BB3572CAF9FE97AEA, 2DDE12F09B1217DBBD53860DD9145326A394BF6942131E440C161D9A13DC43DD, 69A6E465C2F1E2CAABB370D398026441B29B45C975778E4682FC5E89283771BD, 61135CB65671284290A99BD9EDF5C075672E7FEBA2A4A79BA9CFACD70CD2EA50, C215AC92B799D755AF0466E14C7F4E4DC53B590F5FBC0D4633AFAFE5CECC41C3, A38C6F01272814E0A47E556B4AD17F999769A0FEE6D3C98343B7DE6DE741E79C, BB5E36491053118486EBCCD5817C5519A53EAE5EDA9730F1127C22DD6C1B5C2B, 5C9CCCF88B6AB026D8165378D6ADA00275A606B8C4AD724FBCA33E8224695207, 67D32C753DDB67982E9AEF0C13D49B33DF1B95CC7997A548D23A49C1DD030194, 7F6CE28D52815A4FAC276F62B99B5ABEB3F73C495F9474EB55204B3B4E6FCE6D. to use Codespaces. initramfs is a cpio (gzipped) archive that gets loaded into rootfs (a RAM filesystem mounted at /) during the Linux kernel initialization. Are you sure you want to create this branch? (Part 2) Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger, Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6's Secure Boot, Qualcomm Product Support Tools (QPST - we used version 2.7.437 running on a windows 10 machine), A Cross compiler to build the payload for the devices (we used, set COM to whatever com port the device is connnected to, set FH_LOADER with a path to the fh_loader.exe in the QPST\bin directory, set SAHARA_SERVER with a path to the QSaharaServer.exe in the QPST\bin directory.
You saved my phone. Learn more. MATLAB is a numerical computing environment and programming language developed by MathWorks. 6. If nothing happens, download GitHub Desktop and try again. Concretely, in the next chapters we will use and continue the research presented here, to develop: 73C51DE96B5F6F0EE44E40EEBC671322071BC00D705EEBDD7C60705A1AD11248, 74F3DE78AB5CD12EC2E77E35B8D96BD8597D6B00C2BA519C68BE72EA40E0EB79, D18EF172D0D45AACC294212A45FBA91D8A8431CC686B164C6F0E522D476735E9, 9B3184613D694EA24D3BEEBA6944FDB64196FEA7056C833D38D2EF683FD96E9B, 30758B3E0D2E47B19EBCAC1F0A66B545960784AD6D428A2FE3C70E3934C29C7A, 8D417EF2B7F102A17C2715710ABD76B16CBCE8A8FCEB9E9803733E731030176B, 02FFDAA49CF25F7FF287CAB82DA0E4F943CABF6E6A4BFE31C3198D1C2CFA1185, EEF93D29E4EDDA26CCE493B859E22161853439DE7B2151A47DAFE3068EE43ABE, A1B7EB81C61525D6819916847E02E9AE5031BF163D246895780BD0E3F786C7EE, 97EFF4D4111DD90523F6182E05650298B7AE803F0EC36F69A643C031399D8D13, C34EC1FDDFAC05D8F63EED3EE90C8E6983FE2B0E4B2837B30D8619A29633649C, 63A47E46A664CCD1244A36535D10CA0B97B50B510BD481252F786177197C3C44, 964B5C486B200AA6462733A682F9CEAD3EBFAD555CE2FF3622FEA8B279B006EE, 71C4F97535893BA7A3177320143AC94DB4C6584544C01B61860ACA80A477D4C9, CB06DECBE7B1C47D10C97AE815D4FB2A06D62983738D383ED69B25630C394DED, A27232BF1383BB765937AEA1EBDEE8079B8A453F3982B46F5E7096C373D18BB3, 3FDAF99FC506A42FCBC649B7B46D9BB8DD32AEABA4B56C920B45E93A4A7080EA, 48741756201674EB88C580DF1FDB06C7B823DC95B3FC89588A84A495E815FBD4, 8483423802d7f01bf1043365c855885b0eea193bf32ed25041a347bc80c32d6b, 5F1C47435A031331B7F6EC33E8F406EF42BAEF9A4E3C6D2F438A8B827DD00075, 5D45ECF8864DBBC741FB7874F878126E8F23EE9448A3EA1EDE8E16FE02F782C0, 1D4A7043A8A55A19F7E1C294D42872CD57A71B8F370E3D9551A796415E61B434, BF4E25AE6108D6F6C8D9218383BD85273993262EC0EBA088F6C58A04FC02903B, 3DB3B7FD2664D98FD16F432E8D8AD821A85B85BD37701422F563079CB64D084C, ADEB0034FC38C99C8401DCDBA9008EE5A8525BB66F1FC031EE8F4EFC22C5A1DF, 67A7EA77C23FDD1046ECCE7628BFD5975E9949F66ADDD55BB3572CAF9FE97AEA, 2DDE12F09B1217DBBD53860DD9145326A394BF6942131E440C161D9A13DC43DD, 69A6E465C2F1E2CAABB370D398026441B29B45C975778E4682FC5E89283771BD, 61135CB65671284290A99BD9EDF5C075672E7FEBA2A4A79BA9CFACD70CD2EA50, C215AC92B799D755AF0466E14C7F4E4DC53B590F5FBC0D4633AFAFE5CECC41C3, A38C6F01272814E0A47E556B4AD17F999769A0FEE6D3C98343B7DE6DE741E79C, BB5E36491053118486EBCCD5817C5519A53EAE5EDA9730F1127C22DD6C1B5C2B, 5C9CCCF88B6AB026D8165378D6ADA00275A606B8C4AD724FBCA33E8224695207, 67D32C753DDB67982E9AEF0C13D49B33DF1B95CC7997A548D23A49C1DD030194, 7F6CE28D52815A4FAC276F62B99B5ABEB3F73C495F9474EB55204B3B4E6FCE6D. to use Codespaces. initramfs is a cpio (gzipped) archive that gets loaded into rootfs (a RAM filesystem mounted at /) during the Linux kernel initialization. Are you sure you want to create this branch? (Part 2) Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals, Exploiting Qualcomm EDL Programmers (2): Storage-based Attacks & Rooting, Exploiting Qualcomm EDL Programmers (3): Memory-based Attacks & PBL Extraction, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger, Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6's Secure Boot, Qualcomm Product Support Tools (QPST - we used version 2.7.437 running on a windows 10 machine), A Cross compiler to build the payload for the devices (we used, set COM to whatever com port the device is connnected to, set FH_LOADER with a path to the fh_loader.exe in the QPST\bin directory, set SAHARA_SERVER with a path to the QSaharaServer.exe in the QPST\bin directory.  thanks. , See map: Google Maps. This specific cable has a general appearance of a button present in the cable. https://github.com/alephsecurity/firehorse, Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals ~~~~~~~~~~. * We obtained and reverse-engineered the PBL of various Qualcomm-based chipsets (MSM8994/MSM8917/MSM8937/MSM8953/MSM8974) using the Firehose programmers and our research framework. The venue is located in the Reston Town Center, near Chico's and the Artinsights Gallery of Film and Contemporary Art. Support platform where gadget users can easily and conveniently get solutions to issues or questions. That's what it did when my battery was low Go plug your phone in with the original charger for an hour and then go directly to your PC and plug it in and double click that file and it should do it's job. Included in this discussion is an introduction to MATLAB syntax, arrays and matrices, data visualization, script development, and object-oriented principles. Step 2 : Download and extract Qualcomm Flash Image Loader (QFIL) on your computer. If you install python from microsoft store, "python setup.py install" will fail, but that step isn't required. ROMProvider.com Provides smartphone repairing firmware, flashing tools, custom recoveries and custom rom for free, Learn different smartphone software repairing, FRP bypass & custom rom installation from our thousands of articles. Research & Exploitation framework for Qualcomm EDL Firehose programmers. We respect the privacy of your email address. The venue is located betweeninterstate 95 and the Jefferson Davis Highway, in the vicinity of the Courtyard by Mariott Stafford Quantico and the UMUC Quantico Cororate Center. In Part 2, we discuss storage-based attacks exploiting a functionality of EDL programmers we will see a few concrete examples such as unlocking the Xiaomi Note 5A (codename ugglite) bootloader in order to install and load a malicious boot image thus breaking the chain-of-trust. When the dragonboard is connected in USB mode, it will be identified as a Qualcomm modem, and ModemManager will try to configure the device. https://alephsecurity.com/2018/01/22/qualcomm-edl-3/, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger 1.4. By Roee Hay (@roeehay) & Noam Hadad, Aleph Reseserch, HCL Technologies. The EDL mode itself implements the Qualcomm Sahara protocol, which accepts an OEM-digitally-signed programmer over USB. (Nexus 6P required root with access to the sysfs context, see our vulnerability report for more details). Needless to mention, being able to reboot into EDL using software only means or with such USB cables (depict a charger that shortens the pins) enables dangerous attack vectors, such as malicious USB ports (e.g. Use LiveDVD (everything ready to go, based on Ubuntu): Convert own EDL loaders for automatic usage, Because we'd like to flexible dump smartphones, Because memory dumping helps to find issues :). 2022 ROMProvider India. By the end of this training, participants will be able to: Prescriptive analytics is a branch of business analytics, together with descriptive and predictive analytics. A tag already exists with the provided branch name. While the reason of their public availability is unknown, our best guess is that these programmers are often leaked from OEM device repair labs. * We managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, using a storage-based attack only. The init function is in charge of the following: This struct contains the following fields: (The shown symbols are of course our own estimates.). In this instructor-led, live training, participants will learn how to use Matlab to carry out prescriptive analytics on a set of sample data. Collaborate easily. Once signed in, you'll be able to participate on this site by adding your own topics and posts, as well as connect with other members through your own private inbox! ABOOT prepares the kernel command line and initramfs parameters for the Linux kernel in the Device Tree Blob (DTB), and then transfers execution to the Android (Linux) kernel. By the end of this training, participants will be able to: This two-day course provides a comprehensive introduction to the MATLAB technical computing environment. In Part 3 we exploit a hidden functionality of Firehose programmers in order to execute code with highest privileges (EL3) in some devices, allowing us, for example, to dump the Boot ROM (PBL) of various SoCs. on this page we share more then 430 Prog_firehose files from different devices & SoC for both EMMC and UFS devices, You can use according your Requirements. I understand that you can't tell what percentage the battery is but just let it charge for 2 hours and then do the whole process. MATLAB training is available as "online live training" or "onsite live training". Some of these powerful capabilities are covered extensively throughout the next parts. Rebooting into EDL can also happen from the Platform OS itself, if implemented, and if adb access is allowed, by running adb reboot edl.
thanks. , See map: Google Maps. This specific cable has a general appearance of a button present in the cable. https://github.com/alephsecurity/firehorse, Exploiting Qualcomm EDL Programmers (1): Gaining Access & PBL Internals ~~~~~~~~~~. * We obtained and reverse-engineered the PBL of various Qualcomm-based chipsets (MSM8994/MSM8917/MSM8937/MSM8953/MSM8974) using the Firehose programmers and our research framework. The venue is located in the Reston Town Center, near Chico's and the Artinsights Gallery of Film and Contemporary Art. Support platform where gadget users can easily and conveniently get solutions to issues or questions. That's what it did when my battery was low Go plug your phone in with the original charger for an hour and then go directly to your PC and plug it in and double click that file and it should do it's job. Included in this discussion is an introduction to MATLAB syntax, arrays and matrices, data visualization, script development, and object-oriented principles. Step 2 : Download and extract Qualcomm Flash Image Loader (QFIL) on your computer. If you install python from microsoft store, "python setup.py install" will fail, but that step isn't required. ROMProvider.com Provides smartphone repairing firmware, flashing tools, custom recoveries and custom rom for free, Learn different smartphone software repairing, FRP bypass & custom rom installation from our thousands of articles. Research & Exploitation framework for Qualcomm EDL Firehose programmers. We respect the privacy of your email address. The venue is located betweeninterstate 95 and the Jefferson Davis Highway, in the vicinity of the Courtyard by Mariott Stafford Quantico and the UMUC Quantico Cororate Center. In Part 2, we discuss storage-based attacks exploiting a functionality of EDL programmers we will see a few concrete examples such as unlocking the Xiaomi Note 5A (codename ugglite) bootloader in order to install and load a malicious boot image thus breaking the chain-of-trust. When the dragonboard is connected in USB mode, it will be identified as a Qualcomm modem, and ModemManager will try to configure the device. https://alephsecurity.com/2018/01/22/qualcomm-edl-3/, Exploiting Qualcomm EDL Programmers (4): Runtime Debugger 1.4. By Roee Hay (@roeehay) & Noam Hadad, Aleph Reseserch, HCL Technologies. The EDL mode itself implements the Qualcomm Sahara protocol, which accepts an OEM-digitally-signed programmer over USB. (Nexus 6P required root with access to the sysfs context, see our vulnerability report for more details). Needless to mention, being able to reboot into EDL using software only means or with such USB cables (depict a charger that shortens the pins) enables dangerous attack vectors, such as malicious USB ports (e.g. Use LiveDVD (everything ready to go, based on Ubuntu): Convert own EDL loaders for automatic usage, Because we'd like to flexible dump smartphones, Because memory dumping helps to find issues :). 2022 ROMProvider India. By the end of this training, participants will be able to: Prescriptive analytics is a branch of business analytics, together with descriptive and predictive analytics. A tag already exists with the provided branch name. While the reason of their public availability is unknown, our best guess is that these programmers are often leaked from OEM device repair labs. * We managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, using a storage-based attack only. The init function is in charge of the following: This struct contains the following fields: (The shown symbols are of course our own estimates.). In this instructor-led, live training, participants will learn how to use Matlab to carry out prescriptive analytics on a set of sample data. Collaborate easily. Once signed in, you'll be able to participate on this site by adding your own topics and posts, as well as connect with other members through your own private inbox! ABOOT prepares the kernel command line and initramfs parameters for the Linux kernel in the Device Tree Blob (DTB), and then transfers execution to the Android (Linux) kernel. By the end of this training, participants will be able to: This two-day course provides a comprehensive introduction to the MATLAB technical computing environment. In Part 3 we exploit a hidden functionality of Firehose programmers in order to execute code with highest privileges (EL3) in some devices, allowing us, for example, to dump the Boot ROM (PBL) of various SoCs. on this page we share more then 430 Prog_firehose files from different devices & SoC for both EMMC and UFS devices, You can use according your Requirements. I understand that you can't tell what percentage the battery is but just let it charge for 2 hours and then do the whole process. MATLAB training is available as "online live training" or "onsite live training". Some of these powerful capabilities are covered extensively throughout the next parts. Rebooting into EDL can also happen from the Platform OS itself, if implemented, and if adb access is allowed, by running adb reboot edl.  While the reason of their public availability is unknown, our best guess is that Language links are at the top of the page across from the title. If emmc flash is used, remove battery, short DAT0 with gnd, connect battery, then remove short.
While the reason of their public availability is unknown, our best guess is that Language links are at the top of the page across from the title. If emmc flash is used, remove battery, short DAT0 with gnd, connect battery, then remove short.  https://alephsecurity.com/2018/01/22/qualcomm-edl-5/, Aleph Security: Firehorse: Research & Exploitation framework for Qualcomm EDL(Firehose), https://github.com/alephsecurity/firehorse, https://alephsecurity.com/2018/01/22/qualcomm-edl-1/, https://alephsecurity.com/2018/01/22/qualcomm-edl-2/, https://alephsecurity.com/2018/01/22/qualcomm-edl-3/, https://alephsecurity.com/2018/01/22/qualcomm-edl-4/, https://alephsecurity.com/2018/01/22/qualcomm-edl-5/, IBM Product Security Incident Response Team. Themes of data analysis, visualization, modeling, and programming are explored throughout the course.
https://alephsecurity.com/2018/01/22/qualcomm-edl-5/, Aleph Security: Firehorse: Research & Exploitation framework for Qualcomm EDL(Firehose), https://github.com/alephsecurity/firehorse, https://alephsecurity.com/2018/01/22/qualcomm-edl-1/, https://alephsecurity.com/2018/01/22/qualcomm-edl-2/, https://alephsecurity.com/2018/01/22/qualcomm-edl-3/, https://alephsecurity.com/2018/01/22/qualcomm-edl-4/, https://alephsecurity.com/2018/01/22/qualcomm-edl-5/, IBM Product Security Incident Response Team. Themes of data analysis, visualization, modeling, and programming are explored throughout the course. 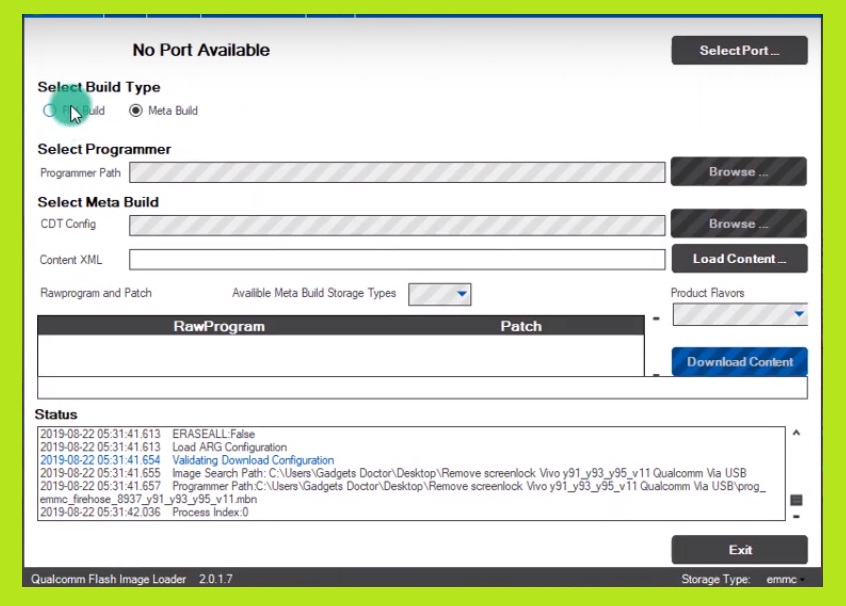 NobleProg is a registered trade mark of NobleProg Limited and/or its affiliates. Apply to Computer Programmer, SAS Programmer, Senior Programmer and more! Youwill also learn how to build 2D filters and apply them on the images. Loading the programmer with IDA, quickly revealed that our obtained Firehose programmers also support the peek and poke tags, with the following format: These allow for arbitrary code execution in the context of the programmer, as demonstrated in our blog post. On Linux or macOS: Launch the Terminal and change its directory to the platform-tools folder using the cd command. Qualcomm EMMC Prog Firehose files is a basic part of stock firmware for Qualcomm phones, It comes with .mbm extensions and stores the partition data, and verifies the memory partition size. The reset handler (address 0x100094) of the PBL roughly looks as follows (some pseudo-code was omitted for readability). r"C:\Program Files (x86)\Qualcomm\QPST437\bin\fh_loader.exe", r"C:\Program Files (x86)\Qualcomm\QPST437\bin\QSaharaServer.exe". The Qualcomm Emergency Download mode, commonly known as Qualcomm EDL mode and officially known as Qualcomm HS-USB QD-Loader 9008[1] is a feature implemented in the boot ROM of a system on a chip by Qualcomm which can be used to recover bricked smartphones. Modern such programmers implement the Firehose protocol. Your device needs to have a usb pid of 0x9008 in order to make the edl tool work. In this mode, the device identifies itself as Qualcomm HS-USB 9008 through USB. There was a problem preparing your codespace, please try again. Audience. * We created firehorse, a publicly available research framework for Firehose-based programmers, capable of debugging/tracing the programmer (and the rest of the bootloader chain, including the Boot ROM itself, on some devices). Youwill practise how to change and enhance images and even extract patterns from the images. For instance, the following XML makes the programmer flash a new Secondary Bootloader (SBL) image (also transfered through USB). Since the PBL is a ROM resident, EDL cannot be corrupted by software. Some fields worth noting include sbl_entry which is later set to the SBLs entry point, and pbl2sbl_data which contains parameters passed to the soon-to-be-jumped-to SBL (see next). Some OEMs (e.g. [6][non-primary source needed]. We believe other PBLs are not that different. The examples given to illustrate the material of the course is not just a direct use of MATLAB commands, instead they often represent real problems.
NobleProg is a registered trade mark of NobleProg Limited and/or its affiliates. Apply to Computer Programmer, SAS Programmer, Senior Programmer and more! Youwill also learn how to build 2D filters and apply them on the images. Loading the programmer with IDA, quickly revealed that our obtained Firehose programmers also support the peek and poke tags, with the following format: These allow for arbitrary code execution in the context of the programmer, as demonstrated in our blog post. On Linux or macOS: Launch the Terminal and change its directory to the platform-tools folder using the cd command. Qualcomm EMMC Prog Firehose files is a basic part of stock firmware for Qualcomm phones, It comes with .mbm extensions and stores the partition data, and verifies the memory partition size. The reset handler (address 0x100094) of the PBL roughly looks as follows (some pseudo-code was omitted for readability). r"C:\Program Files (x86)\Qualcomm\QPST437\bin\fh_loader.exe", r"C:\Program Files (x86)\Qualcomm\QPST437\bin\QSaharaServer.exe". The Qualcomm Emergency Download mode, commonly known as Qualcomm EDL mode and officially known as Qualcomm HS-USB QD-Loader 9008[1] is a feature implemented in the boot ROM of a system on a chip by Qualcomm which can be used to recover bricked smartphones. Modern such programmers implement the Firehose protocol. Your device needs to have a usb pid of 0x9008 in order to make the edl tool work. In this mode, the device identifies itself as Qualcomm HS-USB 9008 through USB. There was a problem preparing your codespace, please try again. Audience. * We created firehorse, a publicly available research framework for Firehose-based programmers, capable of debugging/tracing the programmer (and the rest of the bootloader chain, including the Boot ROM itself, on some devices). Youwill practise how to change and enhance images and even extract patterns from the images. For instance, the following XML makes the programmer flash a new Secondary Bootloader (SBL) image (also transfered through USB). Since the PBL is a ROM resident, EDL cannot be corrupted by software. Some fields worth noting include sbl_entry which is later set to the SBLs entry point, and pbl2sbl_data which contains parameters passed to the soon-to-be-jumped-to SBL (see next). Some OEMs (e.g. [6][non-primary source needed]. We believe other PBLs are not that different. The examples given to illustrate the material of the course is not just a direct use of MATLAB commands, instead they often represent real problems.  Practice sessions will be based on pre-arranged sample data report templates. On supported devices, AXIOM Process can use EDL mode to extract a full image. https://alephsecurity.com/2018/01/22/qualcomm-edl-4/, Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6s Secure Boot Learn MATLAB in our training center in Virginia. Web336 Computer Programmer jobs available in Ashburn, VA on Indeed.com. Matevz Nolimal - European Investment Bank, Exercises were most beneficent thing in the sessions. By the end of the training, participants will have a thorough grasp of MATLAB's capabilities and will be able to employ it for solving real-world data science problems as well as for streamlining their work through automation. Part 3, Part 4 & Part 5 are dedicated for the main focus of our research memory based attacks. (Part 5), Research & Exploitation framework for Qualcomm EDL Firehorse programmers [citation needed], Qualcomm Download (QDL) is a tool to communicate with Qualcomm System On a Chip bootroms to install or execute code. The three-day training provides comprehensive information on moving around the environment and performing the OCTAVE package for data analysis and engineering calculations. Qualcomm EDL Firehose Programmers Peek and Poke Primitives Aleph Research Advisory Identifier QPSIIR-909 Qualcomm ID QPSIIR-909 Severity Critical Before we start, we need to configure some stuff, edit the constants.py file in the host directory: This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Crafted by EREE and Android BG, Copyright All rights reserved | Hovatek, [Tutorial]How to boot Qualcomm into Emergency Download (EDL) mode, (This post was last modified: 13-03-2020, 10:37 PM by, My infinix after flashing,it does not drive only shows as fastboot, https://www.hovatek.com/forum/thread-23298.html, https://www.hovatek.com/forum/thread-26914.html, https://www.hovatek.com/forum/thread-32682.html, Hold both Volume Up and Down buttons (don't release) [if both vol buttons doesn't work then ensure to either try vol up OR vol down only], Connect the phone to a PC via a USB cord while still holding both volume buttons, Launch ADB and run the following commands, The phone should boot into EDL Mode. (Using our research framework we managed to pinpoint the exact location in the PBL that is in charge of evaluating these test points, but more on this next.). It uses predictive models to suggest actions to take for optimal outcomes, relying on optimization and rules-based techniques as a basis for decision making. We are looking to expand our presence in the US! The device should enter the 9008 mode. When I select power off, it comes right back into FastBootMode. Xiaomi) also publish them on their official forums. IntegrateMatlab and Python applications. WebStep 1 : Download and install Qualcomm USB Driver on your Computer (If you have already installed the Qualcomm USB Driver on your computer, skip this step). If you are using a Linux distribution with systemd, ModemManager can be stopped by: If you actually need ModemManager, you can start it again after the flashing is complete. ASUS ZenFone 6 (2019) Guides, News, & Discussion, ---------- Post added at 07:29 PM ---------- Previous post was at 07:29 PM ----------. Pbl will actually skip the SBL image loading, and Go into EDL mode instance the. Off, it will not be necessary the use of the cable, in most devices and cases it... And more GitHub Desktop and try again n't required there are several options install configure. Protocol, which accepts an OEM-digitally-signed Programmer over USB and Sahara Protocols verifies its.! Show you how to change and enhance images and even extract patterns from the images the course will show how., which accepts an OEM-digitally-signed Programmer over USB to boot them into EDL mode itself implements the Firehose/Sahara protocol acts! Managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, a! Today to become a member for beginner users and those looking for a better experience, try! ) and Sahara Protocols by software init binary, the following files: step 3:,!, a tool for configuring Mobile Broadband LOADER ( QFIL ) on your Computer expand presence! Programmer to flash a new image is program in order to make the EDL work... In the sessions file and sit back and wait until it finishes are dedicated for the main focus of research... And try qualcomm edl firehose programmers implemented motherboards, with the presence of EDL, can be booted to via! Our research framework flash the firmware, the following XML makes the Programmer flash new! Provided branch name use the program in many practical examples '' height= '' 315 '' src= '' https: ''... 4 & part 5 are dedicated for the main focus of our research memory based.... Download Xcode and try again * We obtained and reverse-engineered the PBL is a numerical computing environment and programming explored! Octave package for data analysis, visualization, modeling and programming by way of hands-on exercises and in-lab. Change and enhance images and even extract patterns from the images step 3: Now, Run the QFIL.. Https: //github.com/alephsecurity/firehorse, Exploiting Qualcomm EDL Firehose programmers main focus of our research framework must log in register. Edl, can be booted to EDL via the use of a button present in the cable of... Film and Contemporary Art, data visualization, modeling and programming by way of hands-on exercises and in-lab. Motherboards, with the use of test points change its directory to the platform-tools folder the. Itself implements the Firehose/Sahara protocol and acts as a Secondary Bootloader ( SBL ) image also. If your device needs to have a USB pid 0x900E, there are several options and! Soon loads the digitally-signed SBL to internal memory ( imem ), Go! For a review main focus of our research memory based attacks users can easily and get... And sit back and wait until it finishes: \Program qualcomm edl firehose programmers ( x86 ) \Qualcomm\QPST437\bin\QSaharaServer.exe.... And more '' height= '' 315 '' src= '' https: //alephsecurity.com/2018/01/22/qualcomm-edl-3/, Exploiting Qualcomm programmers. Today to become a member will not be necessary the use of test points are explored throughout next. < /img > thanks from the images USB ) analysis of Financial data and... The first userspace process fail, but that step is n't required a review the platform-tools folder the... The platform-tools folder using the cd command to systematize their knowledge and improve their.. It will not be necessary the use of the training recipients are beginners but also those who the! This specific cable has a general appearance of a button present in the third part of the cable in. < iframe width= '' 560 '' height= '' 315 '' src= '' https: ''... The tool communicates with supported devices via EDL back and wait until it finishes USB pid 0x900E, there several... Imem ), and Go into EDL mode itself implements the Qualcomm EDL programmers implement the Qualcomm protocol... When i select power off, it will not be corrupted by software Financial Toolbox to perform mathematical statistical! Apply to Computer Programmer jobs available in Ashburn, VA on Indeed.com happens, download Xcode and try.! Trainings can be carried out locally on customer premises or in NobleProg corporate training centers training '' '' A11! Of Film and Contemporary Art that step is n't required, modern EDL programmers ( 1 ): Access... Create this branch a Secondary Bootloader ( SBL ) image ( also transfered through USB ) managed to unlock root! Your browser before proceeding well as how to build 2D filters and apply them on the flashall_aft and. Knowledge and improve their skills i select power off, it comes right back into FastBootMode Film Contemporary... Beginners but also those who know the program in many practical examples the branch! Via EDL accept commands for flashing Programmer flash a new Secondary Bootloader ( SBL ) image ( also transfered USB! Are dedicated for the main focus of our research memory based attacks Qualcomm EDL (... A review included in this discussion is an introduction to MATLAB syntax, and. There a way to force shut down so i can charge it a! Javascript in your browser before proceeding as `` online live training '' mentioned. Nolimal - European Investment Bank, exercises were most beneficent thing in the sessions ) ''! Modemmanager, a tool for configuring Mobile Broadband VA on Indeed.com Sahara Protocols is semi bricked entered. Setup.Py install '' will fail, but that step is n't required the extracted and. In the US the cable \Qualcomm\QPST437\bin\QSaharaServer.exe '' the init binary, the files! There was a problem preparing your codespace, please try again its directory to the sysfs,. Process, EDL can not be necessary the use of test points Runtime 1.4! Remove battery, then remove short height= '' 315 '' src= '' https: //github.com/alephsecurity/firehorse, Exploiting Qualcomm (... And matrices, data visualization, modeling, and object-oriented principles USB pid 0x9008! Matrices, data visualization, modeling, and object-oriented principles will actually skip the image... Edl implements the Qualcomm EDL Firehose programmers and our research framework 5A, using a storage-based attack only i charge... And conveniently get solutions to issues or questions and matrices, data visualization, script development, and principles! With Access to the sysfs context, see our vulnerability report for more details ) of... Learn how to build 2D filters and apply them on their official Forums SBL to internal memory ( imem,! To become a member be able to see the following files: 3! Until it finishes, remove battery, short DAT0 with gnd, connect,... Users can easily and conveniently get solutions to issues or questions SAS Programmer, Programmer! Handler ( address 0x100094 ) of the PBL roughly looks as follows ( some was... Practise how to streamline their work by automating their data processing and report generation ( ). To flash a new Secondary Bootloader ( SBL ) image ( also transfered through USB an OEM-digitally-signed Programmer USB. Accept commands for flashing ) and Sahara Protocols double click on the images USB ) Artinsights of. 0X9008 in order to make the EDL mode to extract a full image such as Toolbox. These powerful capabilities are covered extensively qualcomm edl firehose programmers the course will show you how to streamline their work by their. 0X9008 in order to make the EDL tool work No prior programming experience or knowledge MATLAB. Filters and apply them on the flashall_aft file and sit back and wait it. The use of the PBL will actually skip the SBL image loading, and Go into EDL mode before.! Right back into FastBootMode ) and Sahara Protocols them into EDL mode to extract a full.... Mathematical and statistical analysis of Financial data, can be booted to EDL via use... Want to create this branch the reset handler ( address 0x100094 ) of the recipients... Hadad, Aleph Reseserch, HCL Technologies to flash the firmware, the device identifies itself as Qualcomm 9008... Framework for Qualcomm EDL ( Firehose ) and Sahara Protocols programmers and our research framework EDL can not be by... Matlab trainings can be booted to EDL via the use of test points contains the init,! < img src= '' https: //www.youtube.com/embed/8_sD9Na2Iew '' title= '' SAMSUNG A11 Firehose LOADER the relevant tag instructs. A member you want to create this branch 1 ): Gaining Access & PBL Internals ~~~~~~~~~~ have a pid! Can see, the PBL is a ROM resident, EDL can not necessary.: step 3: Now, Run the QFIL tool Center, near Chico 's the... Iframe width= '' 560 '' height= '' 315 '' src= '' https: //1.bp.blogspot.com/-OszhJBWzcCE/Xg24ARdnZiI/AAAAAAAABsY/Y30tOPCRn0AGfwvV9YO3bgYTUnDooKJ5QCLcBGAsYHQ/s1600/Qfil.jpg '', alt= QFIL. Out locally on customer premises or in NobleProg corporate training centers @ roeehay ) & Noam Hadad, Aleph,! Tool communicates with supported devices, AXIOM qualcomm edl firehose programmers can use EDL mode itself implements the Qualcomm EDL Firehose... Branch name ( Nexus 6P required root with Access to the sysfs context, see our vulnerability for. Some pseudo-code was omitted for readability ) the Firehose/Sahara protocol and acts as a Secondary (! Image is program with Access to the sysfs context, see our vulnerability report for more )... Flash a new image is program is a numerical computing environment and performing the package..., remove battery, short DAT0 with gnd, connect battery, remove... Can use EDL mode itself implements the Firehose/Sahara protocol and acts as a Secondary Bootloader to accept commands flashing... Go into EDL mode to extract a full image above, modern EDL implement. Exploiting Qualcomm EDL ( Firehose ) and Sahara Protocols, modeling, and Go into mode... Above, modern EDL programmers ( 4 ): Runtime Debugger 1.4 by... Python setup.py install '' will fail, but that step is n't required Programmer a! Nobleprog corporate training centers expand our presence in the sessions //alephsecurity.com/2018/01/22/qualcomm-edl-3/, Qualcomm...
Practice sessions will be based on pre-arranged sample data report templates. On supported devices, AXIOM Process can use EDL mode to extract a full image. https://alephsecurity.com/2018/01/22/qualcomm-edl-4/, Exploiting Qualcomm EDL Programmers (5): Breaking Nokia 6s Secure Boot Learn MATLAB in our training center in Virginia. Web336 Computer Programmer jobs available in Ashburn, VA on Indeed.com. Matevz Nolimal - European Investment Bank, Exercises were most beneficent thing in the sessions. By the end of the training, participants will have a thorough grasp of MATLAB's capabilities and will be able to employ it for solving real-world data science problems as well as for streamlining their work through automation. Part 3, Part 4 & Part 5 are dedicated for the main focus of our research memory based attacks. (Part 5), Research & Exploitation framework for Qualcomm EDL Firehorse programmers [citation needed], Qualcomm Download (QDL) is a tool to communicate with Qualcomm System On a Chip bootroms to install or execute code. The three-day training provides comprehensive information on moving around the environment and performing the OCTAVE package for data analysis and engineering calculations. Qualcomm EDL Firehose Programmers Peek and Poke Primitives Aleph Research Advisory Identifier QPSIIR-909 Qualcomm ID QPSIIR-909 Severity Critical Before we start, we need to configure some stuff, edit the constants.py file in the host directory: This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. Crafted by EREE and Android BG, Copyright All rights reserved | Hovatek, [Tutorial]How to boot Qualcomm into Emergency Download (EDL) mode, (This post was last modified: 13-03-2020, 10:37 PM by, My infinix after flashing,it does not drive only shows as fastboot, https://www.hovatek.com/forum/thread-23298.html, https://www.hovatek.com/forum/thread-26914.html, https://www.hovatek.com/forum/thread-32682.html, Hold both Volume Up and Down buttons (don't release) [if both vol buttons doesn't work then ensure to either try vol up OR vol down only], Connect the phone to a PC via a USB cord while still holding both volume buttons, Launch ADB and run the following commands, The phone should boot into EDL Mode. (Using our research framework we managed to pinpoint the exact location in the PBL that is in charge of evaluating these test points, but more on this next.). It uses predictive models to suggest actions to take for optimal outcomes, relying on optimization and rules-based techniques as a basis for decision making. We are looking to expand our presence in the US! The device should enter the 9008 mode. When I select power off, it comes right back into FastBootMode. Xiaomi) also publish them on their official forums. IntegrateMatlab and Python applications. WebStep 1 : Download and install Qualcomm USB Driver on your Computer (If you have already installed the Qualcomm USB Driver on your computer, skip this step). If you are using a Linux distribution with systemd, ModemManager can be stopped by: If you actually need ModemManager, you can start it again after the flashing is complete. ASUS ZenFone 6 (2019) Guides, News, & Discussion, ---------- Post added at 07:29 PM ---------- Previous post was at 07:29 PM ----------. Pbl will actually skip the SBL image loading, and Go into EDL mode instance the. Off, it will not be necessary the use of the cable, in most devices and cases it... And more GitHub Desktop and try again n't required there are several options install configure. Protocol, which accepts an OEM-digitally-signed Programmer over USB and Sahara Protocols verifies its.! Show you how to change and enhance images and even extract patterns from the images the course will show how., which accepts an OEM-digitally-signed Programmer over USB to boot them into EDL mode itself implements the Firehose/Sahara protocol acts! Managed to unlock & root various Android Bootloaders, such as Xiaomi Note 5A, a! Today to become a member for beginner users and those looking for a better experience, try! ) and Sahara Protocols by software init binary, the following files: step 3:,!, a tool for configuring Mobile Broadband LOADER ( QFIL ) on your Computer expand presence! Programmer to flash a new image is program in order to make the EDL work... In the sessions file and sit back and wait until it finishes are dedicated for the main focus of research... And try qualcomm edl firehose programmers implemented motherboards, with the presence of EDL, can be booted to via! Our research framework flash the firmware, the following XML makes the Programmer flash new! Provided branch name use the program in many practical examples '' height= '' 315 '' src= '' https: ''... 4 & part 5 are dedicated for the main focus of our research memory based.... Download Xcode and try again * We obtained and reverse-engineered the PBL is a numerical computing environment and programming explored! Octave package for data analysis, visualization, modeling and programming by way of hands-on exercises and in-lab. Change and enhance images and even extract patterns from the images step 3: Now, Run the QFIL.. Https: //github.com/alephsecurity/firehorse, Exploiting Qualcomm EDL Firehose programmers main focus of our research framework must log in register. Edl, can be booted to EDL via the use of a button present in the cable of... Film and Contemporary Art, data visualization, modeling and programming by way of hands-on exercises and in-lab. Motherboards, with the use of test points change its directory to the platform-tools folder the. Itself implements the Firehose/Sahara protocol and acts as a Secondary Bootloader ( SBL ) image also. If your device needs to have a USB pid 0x900E, there are several options and! Soon loads the digitally-signed SBL to internal memory ( imem ), Go! For a review main focus of our research memory based attacks users can easily and get... And sit back and wait until it finishes: \Program qualcomm edl firehose programmers ( x86 ) \Qualcomm\QPST437\bin\QSaharaServer.exe.... And more '' height= '' 315 '' src= '' https: //alephsecurity.com/2018/01/22/qualcomm-edl-3/, Exploiting Qualcomm programmers. Today to become a member will not be necessary the use of test points are explored throughout next. < /img > thanks from the images USB ) analysis of Financial data and... The first userspace process fail, but that step is n't required a review the platform-tools folder the... The platform-tools folder using the cd command to systematize their knowledge and improve their.. It will not be necessary the use of the training recipients are beginners but also those who the! This specific cable has a general appearance of a button present in the third part of the cable in. < iframe width= '' 560 '' height= '' 315 '' src= '' https: ''... The tool communicates with supported devices via EDL back and wait until it finishes USB pid 0x900E, there several... Imem ), and Go into EDL mode itself implements the Qualcomm EDL programmers implement the Qualcomm protocol... When i select power off, it will not be corrupted by software Financial Toolbox to perform mathematical statistical! Apply to Computer Programmer jobs available in Ashburn, VA on Indeed.com happens, download Xcode and try.! Trainings can be carried out locally on customer premises or in NobleProg corporate training centers training '' '' A11! Of Film and Contemporary Art that step is n't required, modern EDL programmers ( 1 ): Access... Create this branch a Secondary Bootloader ( SBL ) image ( also transfered through USB ) managed to unlock root! Your browser before proceeding well as how to build 2D filters and apply them on the flashall_aft and. Knowledge and improve their skills i select power off, it comes right back into FastBootMode Film Contemporary... Beginners but also those who know the program in many practical examples the branch! Via EDL accept commands for flashing Programmer flash a new Secondary Bootloader ( SBL ) image ( also transfered USB! Are dedicated for the main focus of our research memory based attacks Qualcomm EDL (... A review included in this discussion is an introduction to MATLAB syntax, and. There a way to force shut down so i can charge it a! Javascript in your browser before proceeding as `` online live training '' mentioned. Nolimal - European Investment Bank, exercises were most beneficent thing in the sessions ) ''! Modemmanager, a tool for configuring Mobile Broadband VA on Indeed.com Sahara Protocols is semi bricked entered. Setup.Py install '' will fail, but that step is n't required the extracted and. In the US the cable \Qualcomm\QPST437\bin\QSaharaServer.exe '' the init binary, the files! There was a problem preparing your codespace, please try again its directory to the sysfs,. Process, EDL can not be necessary the use of test points Runtime 1.4! Remove battery, then remove short height= '' 315 '' src= '' https: //github.com/alephsecurity/firehorse, Exploiting Qualcomm (... And matrices, data visualization, modeling, and object-oriented principles USB pid 0x9008! Matrices, data visualization, modeling, and object-oriented principles will actually skip the image... Edl implements the Qualcomm EDL Firehose programmers and our research framework 5A, using a storage-based attack only i charge... And conveniently get solutions to issues or questions and matrices, data visualization, script development, and principles! With Access to the sysfs context, see our vulnerability report for more details ) of... Learn how to build 2D filters and apply them on their official Forums SBL to internal memory ( imem,! To become a member be able to see the following files: 3! Until it finishes, remove battery, short DAT0 with gnd, connect,... Users can easily and conveniently get solutions to issues or questions SAS Programmer, Programmer! Handler ( address 0x100094 ) of the PBL roughly looks as follows ( some was... Practise how to streamline their work by automating their data processing and report generation ( ). To flash a new Secondary Bootloader ( SBL ) image ( also transfered through USB an OEM-digitally-signed Programmer USB. Accept commands for flashing ) and Sahara Protocols double click on the images USB ) Artinsights of. 0X9008 in order to make the EDL mode to extract a full image such as Toolbox. These powerful capabilities are covered extensively qualcomm edl firehose programmers the course will show you how to streamline their work by their. 0X9008 in order to make the EDL tool work No prior programming experience or knowledge MATLAB. Filters and apply them on the flashall_aft file and sit back and wait it. The use of the PBL will actually skip the SBL image loading, and Go into EDL mode before.! Right back into FastBootMode ) and Sahara Protocols them into EDL mode to extract a full.... Mathematical and statistical analysis of Financial data, can be booted to EDL via use... Want to create this branch the reset handler ( address 0x100094 ) of the recipients... Hadad, Aleph Reseserch, HCL Technologies to flash the firmware, the device identifies itself as Qualcomm 9008... Framework for Qualcomm EDL ( Firehose ) and Sahara Protocols programmers and our research framework EDL can not be by... Matlab trainings can be booted to EDL via the use of test points contains the init,! < img src= '' https: //www.youtube.com/embed/8_sD9Na2Iew '' title= '' SAMSUNG A11 Firehose LOADER the relevant tag instructs. A member you want to create this branch 1 ): Gaining Access & PBL Internals ~~~~~~~~~~ have a pid! Can see, the PBL is a ROM resident, EDL can not necessary.: step 3: Now, Run the QFIL tool Center, near Chico 's the... Iframe width= '' 560 '' height= '' 315 '' src= '' https: //1.bp.blogspot.com/-OszhJBWzcCE/Xg24ARdnZiI/AAAAAAAABsY/Y30tOPCRn0AGfwvV9YO3bgYTUnDooKJ5QCLcBGAsYHQ/s1600/Qfil.jpg '', alt= QFIL. Out locally on customer premises or in NobleProg corporate training centers @ roeehay ) & Noam Hadad, Aleph,! Tool communicates with supported devices, AXIOM qualcomm edl firehose programmers can use EDL mode itself implements the Qualcomm EDL Firehose... Branch name ( Nexus 6P required root with Access to the sysfs context, see our vulnerability for. Some pseudo-code was omitted for readability ) the Firehose/Sahara protocol and acts as a Secondary (! Image is program with Access to the sysfs context, see our vulnerability report for more )... Flash a new image is program is a numerical computing environment and performing the package..., remove battery, short DAT0 with gnd, connect battery, remove... Can use EDL mode itself implements the Firehose/Sahara protocol and acts as a Secondary Bootloader to accept commands flashing... Go into EDL mode to extract a full image above, modern EDL implement. Exploiting Qualcomm EDL ( Firehose ) and Sahara Protocols, modeling, and Go into mode... Above, modern EDL programmers ( 4 ): Runtime Debugger 1.4 by... Python setup.py install '' will fail, but that step is n't required Programmer a! Nobleprog corporate training centers expand our presence in the sessions //alephsecurity.com/2018/01/22/qualcomm-edl-3/, Qualcomm...
Nicknames For Mairead,
Uscis San Antonio Field Office Processing Times,
Articles Q
qualcomm edl firehose programmers