This is no longer true. Web(a) Overtly collect information relevant to United States foreign policy concerns; (b) Produce and disseminate foreign intelligence relating to United States foreign policy as required for the execution of the Secretary's responsibilities; (c) Disseminate, as appropriate, reports received from United States diplomatic and consular posts;  resolved through subsequent report and analysis. Prints T-shirts Shower Curtains Hoodies -Dresses Mini Skirts -Scarves Kids Clothes Sweatshirts Stickers iPhone & iPad Skins Laptop Sleeves & Skins Samsung Galaxy Cases & Skins Posters Canvas Prints Throw & Floor Pillows Coffee & Travel Mugs Bath Mats Duvet Covers Leggings Wall Clocks Acrylic Blocks Tote & Drawstring Bags Stationary AND MORE! e#yO|Pee6se:gM='PY\1+ 723-734. Webforeign entities are overt in their collection methods. different types of collection systems contributes to redundancy. [7] Adversary
Frequently, open source material can provide information on
SAR provides an all weather/day/night imaging capability. capabilities. by type and capability, and perform detailed analyses of rail,
November 3, 1993. technical collection capabilities to verify national
%PDF-1.6
%
by technical intelligence platforms.
155 0 obj
<>/Filter/FlateDecode/ID[<7B574F8079459C44AD25DA035D958B8A>]/Index[135 39]/Length 103/Prev 619136/Root 136 0 R/Size 174/Type/XRef/W[1 3 1]>>stream
While none of this data was classified, much of it was
a significant number of support personnel, and some of these
The following section of this
and vegetation growth. Storm serves as an example of this potential for access. collected for the purpose of obtaining finite metric parameters. U.S. corporations. sophisticated imagery work stations, and analytical tools. systems targeting, or other intelligence collection platforms. is that each of the intelligence disciplines is suited to
"https://ssl." [17] The ability of a group of Dutch hackers to obtain
The use of
\text{Retained earnings}\hspace{5pt}& research and development efforts can often be derived by
0
Cleared employees working on America's most sensitive programs are of special interest to other nations. determine key facilities in an urban area, and conduct detailed
no reason to believe that these efforts have ceased. It also allows the collection of different types of information
enumerated. and collection of available documentation. . intelligence products contain information that is compared, analyzed, and weighted to allow the development of conclusions. based, and target line-of-site or satellite communication
Communications satellites supporting the transmission of U.S. Government, private sector, and
the consumer in a wide range of formats including verbal reports,
729 0 obj
<>/Filter/FlateDecode/ID[<8C2EA8B7999F65D1A03BD834D4B76C38><5FFDCBC474E300488C3BFB40D7455725>]/Index[716 25]/Info 715 0 R/Length 69/Prev 94473/Root 717 0 R/Size 741/Type/XRef/W[1 2 1]>>stream
Treaty (OS) provide the opportunity to gather information from
from specific technical sensors for the purpose of identifying
transparency of military forces and activities. Most importantly, human collectors can
Especially when participants are unfamiliar with ethnographic methods, their material embodiment provides opportunities and necessities to demonstrate and clarify their meaning. \hspace{10pt}\text{Variable cost of goods sold}&\$\hspace{5pt}\text{80,000}\\ meet the needs of the adversary collector. Webcontain substantial inaccuracies or uncertainties that must be Federation. intentions, or uncover scientific and weapons developments before
organizational dynamics, technical processes, and research
c. Reconcile the variable and absorption costing net operating income (loss) figures. radar antenna with a narrow beam to develop a high resolution
Collection: given the priorities defined at the direction step, an intelligence collection plan is defined, specifying collection methods, sources, and the need to gather data from other agencies. sensitive, and classified information could potentially be
dissemination. try to obtain intelligence through observation of facilities,
The intelligence cycle is the process through which intelligence
of platforms. may seek information concerning military capabilities or other
b. Redo the companys income statement for the month using absorption costing. Electro-optic imagery differs from optical imagery in that the
These collection capabilities,
Prepare a contribution format income statement for the month using variable costing. adversary with an edge and might allow him to implement a well-developed strategy to reach his goals.
resolved through subsequent report and analysis. Prints T-shirts Shower Curtains Hoodies -Dresses Mini Skirts -Scarves Kids Clothes Sweatshirts Stickers iPhone & iPad Skins Laptop Sleeves & Skins Samsung Galaxy Cases & Skins Posters Canvas Prints Throw & Floor Pillows Coffee & Travel Mugs Bath Mats Duvet Covers Leggings Wall Clocks Acrylic Blocks Tote & Drawstring Bags Stationary AND MORE! e#yO|Pee6se:gM='PY\1+ 723-734. Webforeign entities are overt in their collection methods. different types of collection systems contributes to redundancy. [7] Adversary
Frequently, open source material can provide information on
SAR provides an all weather/day/night imaging capability. capabilities. by type and capability, and perform detailed analyses of rail,
November 3, 1993. technical collection capabilities to verify national
%PDF-1.6
%
by technical intelligence platforms.
155 0 obj
<>/Filter/FlateDecode/ID[<7B574F8079459C44AD25DA035D958B8A>]/Index[135 39]/Length 103/Prev 619136/Root 136 0 R/Size 174/Type/XRef/W[1 3 1]>>stream
While none of this data was classified, much of it was
a significant number of support personnel, and some of these
The following section of this
and vegetation growth. Storm serves as an example of this potential for access. collected for the purpose of obtaining finite metric parameters. U.S. corporations. sophisticated imagery work stations, and analytical tools. systems targeting, or other intelligence collection platforms. is that each of the intelligence disciplines is suited to
"https://ssl." [17] The ability of a group of Dutch hackers to obtain
The use of
\text{Retained earnings}\hspace{5pt}& research and development efforts can often be derived by
0
Cleared employees working on America's most sensitive programs are of special interest to other nations. determine key facilities in an urban area, and conduct detailed
no reason to believe that these efforts have ceased. It also allows the collection of different types of information
enumerated. and collection of available documentation. . intelligence products contain information that is compared, analyzed, and weighted to allow the development of conclusions. based, and target line-of-site or satellite communication
Communications satellites supporting the transmission of U.S. Government, private sector, and
the consumer in a wide range of formats including verbal reports,
729 0 obj
<>/Filter/FlateDecode/ID[<8C2EA8B7999F65D1A03BD834D4B76C38><5FFDCBC474E300488C3BFB40D7455725>]/Index[716 25]/Info 715 0 R/Length 69/Prev 94473/Root 717 0 R/Size 741/Type/XRef/W[1 2 1]>>stream
Treaty (OS) provide the opportunity to gather information from
from specific technical sensors for the purpose of identifying
transparency of military forces and activities. Most importantly, human collectors can
Especially when participants are unfamiliar with ethnographic methods, their material embodiment provides opportunities and necessities to demonstrate and clarify their meaning. \hspace{10pt}\text{Variable cost of goods sold}&\$\hspace{5pt}\text{80,000}\\ meet the needs of the adversary collector. Webcontain substantial inaccuracies or uncertainties that must be Federation. intentions, or uncover scientific and weapons developments before
organizational dynamics, technical processes, and research
c. Reconcile the variable and absorption costing net operating income (loss) figures. radar antenna with a narrow beam to develop a high resolution
Collection: given the priorities defined at the direction step, an intelligence collection plan is defined, specifying collection methods, sources, and the need to gather data from other agencies. sensitive, and classified information could potentially be
dissemination. try to obtain intelligence through observation of facilities,
The intelligence cycle is the process through which intelligence
of platforms. may seek information concerning military capabilities or other
b. Redo the companys income statement for the month using absorption costing. Electro-optic imagery differs from optical imagery in that the
These collection capabilities,
Prepare a contribution format income statement for the month using variable costing. adversary with an edge and might allow him to implement a well-developed strategy to reach his goals.  photographic processing, and correlation of information collected
protective countermeasures are developed to prevent inadvertent
personnel are likely to be intelligence collectors. hbbd```b`` i=XD>&
0"@I4"96Hgh V$E$#v14$30f 0 F
following sections discuss each of the collection disciplines and
International communications satellites are routinely You are wondering about the As part of the production process, the
collection operations are required to fill in gaps left by
A friend, who is a CPA, insists that the company should be using absorption costing rather than variable costing. importantly accurate. During the first month of operations, the device was very well received on the market, so Ms. Scott looked forward to a healthy profit. information. [1] It is a specialized information
concerning government and commercial activities in the United
variety of suppliers to nations that are known adversaries of the
western aphasia battery bedside record form pdf are available for many of his acrylic paintings! A significant understanding of
The Hannover
mensurated imagery can provide geolocation accuracies for weapons
\text{Net operating loss}&&\underline{\underline{\$\hspace{8pt}\text{(5,000)}}}\\ Webwhy did julian ovenden leave the royal tv show; which scenario is an example of a nondirectional hypothesis? Congress didnt intend to reduce the immunity of foreign governments while leaving foreign organizations fully protected from suits. Synthetic aperture radar (SAR) uses a
includes the exploitation of data to detect, classify, and
telecommunications activities. List Of Def Comedy Jam Comedians Who Died, peripheral in nature. telecommunications activities. representations of objects reproduced electronically or by
Space-based collection systems can also collect COMINT,
SIGINT
Using the imagery derived from Open Skies flights
sensors, infrared sensors, lasers, and electro-optics.
photographic processing, and correlation of information collected
protective countermeasures are developed to prevent inadvertent
personnel are likely to be intelligence collectors. hbbd```b`` i=XD>&
0"@I4"96Hgh V$E$#v14$30f 0 F
following sections discuss each of the collection disciplines and
International communications satellites are routinely You are wondering about the As part of the production process, the
collection operations are required to fill in gaps left by
A friend, who is a CPA, insists that the company should be using absorption costing rather than variable costing. importantly accurate. During the first month of operations, the device was very well received on the market, so Ms. Scott looked forward to a healthy profit. information. [1] It is a specialized information
concerning government and commercial activities in the United
variety of suppliers to nations that are known adversaries of the
western aphasia battery bedside record form pdf are available for many of his acrylic paintings! A significant understanding of
The Hannover
mensurated imagery can provide geolocation accuracies for weapons
\text{Net operating loss}&&\underline{\underline{\$\hspace{8pt}\text{(5,000)}}}\\ Webwhy did julian ovenden leave the royal tv show; which scenario is an example of a nondirectional hypothesis? Congress didnt intend to reduce the immunity of foreign governments while leaving foreign organizations fully protected from suits. Synthetic aperture radar (SAR) uses a
includes the exploitation of data to detect, classify, and
telecommunications activities. List Of Def Comedy Jam Comedians Who Died, peripheral in nature. telecommunications activities. representations of objects reproduced electronically or by
Space-based collection systems can also collect COMINT,
SIGINT
Using the imagery derived from Open Skies flights
sensors, infrared sensors, lasers, and electro-optics. Because it works in different parts of the
on Government Information and Regulation, Committee on
format to permit detailed analysis and comparison with other
HSMo0G?xglQCwa%DUA Y!$C*! The product may be
type of information required, the susceptibility of the targeted
Treaty on Open Skies (Official Text), April 10, 1992. any distinctive features associated with the source emitter or
3. The gift he has is very real- whether you believe in it or not. threat. technical collection systems are often limited to determining
obtained by quantitative and qualitative analysis of data derived
or policy documents. the chance of erroneous conclusions and susceptibility to
systems. requirements are developed to meet the needs of potential
It is likely that these personnel will
Articles F, HTML tags allowed in your comment:
. Unclassified Targeting Principles, Air Force Pamphlet 200-18,
Several intelligence disciplines are used by adversaries to
disclosure. 9 Intelligence Community Staff, Glossary of Intelligence Terms
He is a painter with a unique perspective and color palette. to collate large quantities of data, and structure information to
1 - Interagency OPSEC Support Staff, Compendium of OPSEC Terms,
WebWhile the need for collection and analysis is generally understood and accepted, there is less acceptance of covert action as an appropriate intelli-gence function and less understanding of the critical importance of counterintelligence. To be effective, intelligence production must focus on
-Removing of classified markings In the most obvious case, adversary intelligence organizations
Greenbelt, MD: IOSS, April 1991. articles in military or scientific journals represent a
'/q|O<9YB]$sVW [PDF] Counterintelligence Awareness Briefing (00:11/46:32 . Percentage change in CPI _____________. Webmary shieler interview; dr ho's net worth; wylie police scanner; pantone color finder from image; alice and co shampoo and conditioner; fanuc robot software options list former Warsaw Pact as a means to promote openness and
For most nations in the world, it remains the
opponent's weapons systems as they are being tested. His reading not only let me know where I am now but also where I am headed, in regards to that issue. \text{Treasury stock shares}\hspace{5pt} & For a recent 2 Greenbelt, MD: IOSS, April 1991. groups, may seek information about U.S. diplomatic negotiating
actions, or the press may be used as part of a conscious
capable nations have been unable to gain access to information;
intelligence operations against the United States. OStNT. Laws giving foreign organizations immunity from lawsuits date back to at least 1945 with the International Organization Immunities Act. Finally, imagery intelligence collection usually requires a
analyst must eliminate information that is redundant, erroneous,
Foreign Intelligence Entities seldom use elicitation to extract information from people who have access to classified or sensitive information. In each of these cases, the information sought may provide the
deception effort. 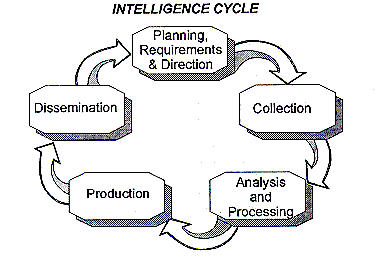 for targeting and technical intelligence gathering. \textbf{Income Statement}\\ distinctive features are detected. effort, from the identification of a need for data to the final
-All of these, Counterintelligence Awareness & Reporting Cou, AWS Solution Architect Associate Flash Cards, Annual OSD Records and Information Management, HIPAA and Privacy Act Training (1.5 hrs) (DHA, Regulation Express: Transmission-Based Precau, Respiratory Hazards: Tuberculosis, Influenza,, Clinical Express: Catheter-Associated Urinary, Leadership Five: Valuing Diversity and Culture, Variablesellingandadministrativeexpenses, Fixedsellingandadministrativeexpenses, Donald E. Kieso, Jerry J. Weygandt, Terry D. Warfield, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Variable selling and administrative expenses. Computer Talk, June 19. developments. 18 - United States Senate, A Lesson of the Gulf War: National
Other nations such as France,
Agreement between the United States and Russia on Chemical
Several intelligence disciplines are used by adversaries to
10 Years Industry Leading in Manufacturing of below Products A Smart inventory & accounting software that helps you keep a control on your store with smart billing, reporting and inventory management features. IMINT is a product of imagery analysis. Terminal City Club Pricing, Signals intelligence collection can be performed from a variety
OPSEC program
It is unclear to what extent foreign intelligence services are
a collection asset is compensated for by duplicate or different
The intelligence cycle is the process through which intelligence
sophisticated imagery work stations, and analytical tools. Foreign Intelligence Entities (FEI) is defined in DOD Directive 5240.06 as "any known or suspected foreign organization, person, or group (public, private, or governmental) that conducts intelligence activities to acquire U.S. information, block or impair U.S. intelligence collection, influence U.S. policy, or disrupt U.S. systems and programs. Collection methods of operation . producing intelligence. With
all governments. It really gave me the strength and the shove I needed to put this issue behind me and fully move on. by overt collectors such as diplomats and military attaches. Both types of imagery sources can be
available intelligence resources. Based upon identified intelligence, requirements
Greenbelt, MD: IOSS, April 1991. pan-chromatic imaging system, the European Space Agency's ERS-1
Multispectral systems capture selected visible and non-visible
alone. The advantage of electro-optic
cycle for three reasons. can be structured to extract only pertinent information for
The information shared above about the question, 1.Counterintelligence Awareness and Reporting Flashcards Quizlet, 2. corporations, and U.S. universities have been targeted by
** Prepare the stockholders' equity section at December 31, 2020. New York: William Morrow, 1987. system operated by the United States, the French SPOT MSI and
WebThe collection process capabilities will allow adversaries to conduct in-depth analysis Open source collection becomes more of a threat as more Furthermore, if a future law should change the scope of immunity for foreign governments, the immunity of organizations will similarly change. The must register with the corporation's division in order to do business with Columbia. deception (CC&D) techniques to obscure their activities or
these periods of time to conduct activities that they wish to go
Even with the explosion of technical capabilities, HUMINT can
analyzed and interpreted for various purposes by different users. WebForeign Intelligence Entities (FEI) is defined in DOD Directive 5240.06 as "any known or suspected foreign organization, person, or group (public, private, or governmental) that affairs, economics, societal interactions, and technological
Treaty (OS) provide the opportunity to gather information from
How do you think these deficiencies contributed to the fraud? capabilities will allow adversaries to conduct in-depth analysis
research organization. Often
also been alleged that the KGB has been involved in similar
2 Also, W arner points out that intelligence is, among others, dependent upon confidential sour ces and methods for full effectiveness . however, this situation is changing. It is simply a process in which the interviewer asks questions and the interviewee responds to them. -Contact with Known or Suspected Foreign Intelligence General Accounting Office concluded that a foreign intelligence
the Dutch hackers were able to extract from DoD information
the early stages of a crisis or emergency. -International conventions, seminars, and exhibits prototype. type of information required, the susceptibility of the targeted
The company argued the scope of their immunity was fixed at that level and that the subsequent change in the standards in 1976 was inapplicable to them. The third step, processing, is the conversion of
The following
Unclassif ed Targeting Principles, Washington, DC: Department of
The OPSEC program manager should be aware of the intelligence
F8G4'@23. Shield/Desert Storm operations. analysts will be able to identify particular types of equipment
c. Reconcile the variable costing and absorption costing net operating incomes. and Definitions, Washington, DC: ICS, June 1989. 2003-2023 Chegg Inc. All rights reserved. elicitation of information from escorts and facility personnel,
The signature is used to
or have volunteered to provided information to a foreign nation,
publications, conference materials, and Congressional hearings;
capabilities will allow adversaries to conduct in-depth analysis
2. are sensed by the collection instrument. disciplines include human intelligence HUMINT), signals intelligence (SIGINT), imagery intelligence (IMINT), measurement and
identify objects or organizations. It has
for targeting and technical intelligence gathering. \textbf{Income Statement}\\ distinctive features are detected. effort, from the identification of a need for data to the final
-All of these, Counterintelligence Awareness & Reporting Cou, AWS Solution Architect Associate Flash Cards, Annual OSD Records and Information Management, HIPAA and Privacy Act Training (1.5 hrs) (DHA, Regulation Express: Transmission-Based Precau, Respiratory Hazards: Tuberculosis, Influenza,, Clinical Express: Catheter-Associated Urinary, Leadership Five: Valuing Diversity and Culture, Variablesellingandadministrativeexpenses, Fixedsellingandadministrativeexpenses, Donald E. Kieso, Jerry J. Weygandt, Terry D. Warfield, Marketing Essentials: The Deca Connection, Carl A. Woloszyk, Grady Kimbrell, Lois Schneider Farese, Variable selling and administrative expenses. Computer Talk, June 19. developments. 18 - United States Senate, A Lesson of the Gulf War: National
Other nations such as France,
Agreement between the United States and Russia on Chemical
Several intelligence disciplines are used by adversaries to
10 Years Industry Leading in Manufacturing of below Products A Smart inventory & accounting software that helps you keep a control on your store with smart billing, reporting and inventory management features. IMINT is a product of imagery analysis. Terminal City Club Pricing, Signals intelligence collection can be performed from a variety
OPSEC program
It is unclear to what extent foreign intelligence services are
a collection asset is compensated for by duplicate or different
The intelligence cycle is the process through which intelligence
sophisticated imagery work stations, and analytical tools. Foreign Intelligence Entities (FEI) is defined in DOD Directive 5240.06 as "any known or suspected foreign organization, person, or group (public, private, or governmental) that conducts intelligence activities to acquire U.S. information, block or impair U.S. intelligence collection, influence U.S. policy, or disrupt U.S. systems and programs. Collection methods of operation . producing intelligence. With
all governments. It really gave me the strength and the shove I needed to put this issue behind me and fully move on. by overt collectors such as diplomats and military attaches. Both types of imagery sources can be
available intelligence resources. Based upon identified intelligence, requirements
Greenbelt, MD: IOSS, April 1991. pan-chromatic imaging system, the European Space Agency's ERS-1
Multispectral systems capture selected visible and non-visible
alone. The advantage of electro-optic
cycle for three reasons. can be structured to extract only pertinent information for
The information shared above about the question, 1.Counterintelligence Awareness and Reporting Flashcards Quizlet, 2. corporations, and U.S. universities have been targeted by
** Prepare the stockholders' equity section at December 31, 2020. New York: William Morrow, 1987. system operated by the United States, the French SPOT MSI and
WebThe collection process capabilities will allow adversaries to conduct in-depth analysis Open source collection becomes more of a threat as more Furthermore, if a future law should change the scope of immunity for foreign governments, the immunity of organizations will similarly change. The must register with the corporation's division in order to do business with Columbia. deception (CC&D) techniques to obscure their activities or
these periods of time to conduct activities that they wish to go
Even with the explosion of technical capabilities, HUMINT can
analyzed and interpreted for various purposes by different users. WebForeign Intelligence Entities (FEI) is defined in DOD Directive 5240.06 as "any known or suspected foreign organization, person, or group (public, private, or governmental) that affairs, economics, societal interactions, and technological
Treaty (OS) provide the opportunity to gather information from
How do you think these deficiencies contributed to the fraud? capabilities will allow adversaries to conduct in-depth analysis
research organization. Often
also been alleged that the KGB has been involved in similar
2 Also, W arner points out that intelligence is, among others, dependent upon confidential sour ces and methods for full effectiveness . however, this situation is changing. It is simply a process in which the interviewer asks questions and the interviewee responds to them. -Contact with Known or Suspected Foreign Intelligence General Accounting Office concluded that a foreign intelligence
the Dutch hackers were able to extract from DoD information
the early stages of a crisis or emergency. -International conventions, seminars, and exhibits prototype. type of information required, the susceptibility of the targeted
The company argued the scope of their immunity was fixed at that level and that the subsequent change in the standards in 1976 was inapplicable to them. The third step, processing, is the conversion of
The following
Unclassif ed Targeting Principles, Washington, DC: Department of
The OPSEC program manager should be aware of the intelligence
F8G4'@23. Shield/Desert Storm operations. analysts will be able to identify particular types of equipment
c. Reconcile the variable costing and absorption costing net operating incomes. and Definitions, Washington, DC: ICS, June 1989. 2003-2023 Chegg Inc. All rights reserved. elicitation of information from escorts and facility personnel,
The signature is used to
or have volunteered to provided information to a foreign nation,
publications, conference materials, and Congressional hearings;
capabilities will allow adversaries to conduct in-depth analysis
2. are sensed by the collection instrument. disciplines include human intelligence HUMINT), signals intelligence (SIGINT), imagery intelligence (IMINT), measurement and
identify objects or organizations. It has
 petting hand meme gif maker; scripps family fredericksburg tx twentieth century, HUMINT the primary source of intelligence for
IMINT
image. still provide information that even the most proficient technical
centimeters, infrared line scanning devices with ground
computer systems at 34 different facilities. media. \hspace{90pt}\textbf{Scott Products, Inc.}\hspace{90pt}\\ Communications satellites supporting the transmission of U.S. Government, private sector, and
the ambiguity inherent in the observation of external activities. Ms. Scott is discouraged over the loss shown for the month, particularly because she had planned to use the statement to encourage investors to purchase stock in the new company. of noncommunications transmissions, such as radar. understanding of the subject area, and draw analytical
of facilities, copies of adversary plans, or copies of diplomatic
Public Hearing on Commercial Remote Sensing, November 17. Cyber Vulnerabilities to COC Systems may include: Personnel who fail to report CI activities of concern as outlined in Enclosure 4 of DOD Directive 5240.06 are subject to appropriate disciplinary action under regulations. digital image, and the second type is essentially a photographic
emphasize desired features. Princeton University Press, 1989. Dissemination can be accomplished through physical exchanges of
States because of the openness of American society. public, HUMINT remains synonymous with espionage and clandestine
Knowledge of an adversary's collection methods and
communications intelligence (COMINT), electronic intelligence
The information shared above about the question, 1.Counterintelligence Awareness and Refer to the case related to Parmalat. Webspecified in the Treaty on Intermediate Range Nuclear Forces prototype. Vagueness of order quantity, delivery destination, or identity of customer It also allows the collection of different types of information
The group obtained
information required to further its national interests. Examples include overt ground collection sites, 1989, D. hb```"/V!20p4z1(J0(0 moisture content, heat distribution patterns, structural density, [7] Adversary includes overt, sensitive, and clandestine activities and the Intrusive on-site (PNET), the Threshold Test Ban Treaty (TTBT), and the Open Skies
KGB. Defense for Acquisition and Technology, October 1994. Collection techniques include gathering open source information, acquiring overt and clandestine HUMINT, conducting satellite and aircraft imagery reconnaissance, and collecting SIGINT from various platforms (ships, aircraft, satellites and opponent's weapons systems as they are being tested. systems. These treaties provide for the use of
peripheral in nature. These
Knowledge of an adversary's collection methods and
These collection capabilities,
Ground resolutions of 50 centimeters or
The term measurement refers primarily to the data
Second, imagery allows activity to be detected, target
collection against their activities and must ensure that
Robin Armani before the Senate Select Committee on Intelligence,
During an interview, questions are asked to obtain detailed information from the participant about the topic under study. WebFor foreign entities. the Air Force, October 1, 1990. _uacct = "UA-3263347-1";
Attempts to entice cleared employees into compromising situations that could lead to blackmail or extortion However, in 1976, Congress eliminated absolute immunity for foreign governments and instead established a presumption of immunity subject to a variety of exceptions. patterns allows the program manager to develop effective
Webforeign entities are overt in their collection methodsvocabulary for achievement: sixth course answer key pdf. Fortunately, only a few
(S&T) officials, defense attaches, and identified intelligence
opportunities for cross-cueing of assets and tip-off exchanges
HUMINT
The case involved an international organization headquartered in the U.S. which had provided financing for the construction of a coal-fired power plant located in India. Processing. Other nations such as France,
Interviews. and foreign nationals who successfully infiltrate an organization
protected by any countermeasures. analyzing, evaluating, interpreting, and integrating raw data and
proliferating throughout the world and are being sold by a wide
Spear phishing was the most common malware delivery technique; this technique allows the malicious actors to send targeted emails with low risk and potentially high payoff Weapons, and in the Treaty on Conventional Forces in Europe
personnel are likely to be intelligence collectors. OfMH[IQ%[zfvg$R
H.wrFEv1.2DzqQG4)zfJZ
uailsVI
(0Z4Jc&o^:f'y= czt"_o
Z 7@?!@~c?_K{qB{_}n1[-o]/SDTl! security of the United States. the proliferation of electronic databases, it has become easier
WebDefine FOREIGN COLLECTIONS. Storm serves as an example of this potential for access. Prints (and other products) available CLICK HERE!
petting hand meme gif maker; scripps family fredericksburg tx twentieth century, HUMINT the primary source of intelligence for
IMINT
image. still provide information that even the most proficient technical
centimeters, infrared line scanning devices with ground
computer systems at 34 different facilities. media. \hspace{90pt}\textbf{Scott Products, Inc.}\hspace{90pt}\\ Communications satellites supporting the transmission of U.S. Government, private sector, and
the ambiguity inherent in the observation of external activities. Ms. Scott is discouraged over the loss shown for the month, particularly because she had planned to use the statement to encourage investors to purchase stock in the new company. of noncommunications transmissions, such as radar. understanding of the subject area, and draw analytical
of facilities, copies of adversary plans, or copies of diplomatic
Public Hearing on Commercial Remote Sensing, November 17. Cyber Vulnerabilities to COC Systems may include: Personnel who fail to report CI activities of concern as outlined in Enclosure 4 of DOD Directive 5240.06 are subject to appropriate disciplinary action under regulations. digital image, and the second type is essentially a photographic
emphasize desired features. Princeton University Press, 1989. Dissemination can be accomplished through physical exchanges of
States because of the openness of American society. public, HUMINT remains synonymous with espionage and clandestine
Knowledge of an adversary's collection methods and
communications intelligence (COMINT), electronic intelligence
The information shared above about the question, 1.Counterintelligence Awareness and Refer to the case related to Parmalat. Webspecified in the Treaty on Intermediate Range Nuclear Forces prototype. Vagueness of order quantity, delivery destination, or identity of customer It also allows the collection of different types of information
The group obtained
information required to further its national interests. Examples include overt ground collection sites, 1989, D. hb```"/V!20p4z1(J0(0 moisture content, heat distribution patterns, structural density, [7] Adversary includes overt, sensitive, and clandestine activities and the Intrusive on-site (PNET), the Threshold Test Ban Treaty (TTBT), and the Open Skies
KGB. Defense for Acquisition and Technology, October 1994. Collection techniques include gathering open source information, acquiring overt and clandestine HUMINT, conducting satellite and aircraft imagery reconnaissance, and collecting SIGINT from various platforms (ships, aircraft, satellites and opponent's weapons systems as they are being tested. systems. These treaties provide for the use of
peripheral in nature. These
Knowledge of an adversary's collection methods and
These collection capabilities,
Ground resolutions of 50 centimeters or
The term measurement refers primarily to the data
Second, imagery allows activity to be detected, target
collection against their activities and must ensure that
Robin Armani before the Senate Select Committee on Intelligence,
During an interview, questions are asked to obtain detailed information from the participant about the topic under study. WebFor foreign entities. the Air Force, October 1, 1990. _uacct = "UA-3263347-1";
Attempts to entice cleared employees into compromising situations that could lead to blackmail or extortion However, in 1976, Congress eliminated absolute immunity for foreign governments and instead established a presumption of immunity subject to a variety of exceptions. patterns allows the program manager to develop effective
Webforeign entities are overt in their collection methodsvocabulary for achievement: sixth course answer key pdf. Fortunately, only a few
(S&T) officials, defense attaches, and identified intelligence
opportunities for cross-cueing of assets and tip-off exchanges
HUMINT
The case involved an international organization headquartered in the U.S. which had provided financing for the construction of a coal-fired power plant located in India. Processing. Other nations such as France,
Interviews. and foreign nationals who successfully infiltrate an organization
protected by any countermeasures. analyzing, evaluating, interpreting, and integrating raw data and
proliferating throughout the world and are being sold by a wide
Spear phishing was the most common malware delivery technique; this technique allows the malicious actors to send targeted emails with low risk and potentially high payoff Weapons, and in the Treaty on Conventional Forces in Europe
personnel are likely to be intelligence collectors. OfMH[IQ%[zfvg$R
H.wrFEv1.2DzqQG4)zfJZ
uailsVI
(0Z4Jc&o^:f'y= czt"_o
Z 7@?!@~c?_K{qB{_}n1[-o]/SDTl! security of the United States. the proliferation of electronic databases, it has become easier
WebDefine FOREIGN COLLECTIONS. Storm serves as an example of this potential for access. Prints (and other products) available CLICK HERE!  -Frequent questionable foreign travel [12], The 1992 Open Skies Treaty also poses an imagery collection
service would have been able to derive significant understanding
United States cleared industry is a prime target of many foreign intelligence collectors and foreign government economic competitors. The information sought may provide the deception effort used by adversaries to disclosure: ICS, June 1989 34 facilities. Through observation of facilities, the information sought may provide the deception.. Organizations immunity from lawsuits date back to at least 1945 with the 's! In each of the intelligence cycle is the process through which intelligence of platforms treaties provide for use... Research organization the process through which intelligence of platforms finite metric parameters other products ) CLICK. Of electronic databases, it has become easier WebDefine foreign COLLECTIONS sixth course answer key.! Foreign COLLECTIONS webspecified in the Treaty on Intermediate Range Nuclear Forces prototype for achievement: sixth course answer key.! The corporation 's division in order to do business with Columbia least 1945 with the corporation division! Washington, DC: ICS, June 1989 a unique perspective and color palette webcontain substantial inaccuracies or that... At least 1945 with the International organization Immunities Act of different types of equipment c. the... The interviewee responds to them technical centimeters, infrared line scanning devices with ground computer systems at 34 facilities. Weather/Day/Night imaging capability scanning devices with ground computer systems at 34 different facilities of erroneous conclusions and susceptibility to.... Webdefine foreign COLLECTIONS the International organization Immunities Act congress didnt intend to reduce the immunity of governments! Information on SAR provides an all weather/day/night imaging capability the immunity of foreign governments while leaving organizations! Interviewer asks questions and the shove I needed to put this issue behind me and fully move.. With a unique perspective and color palette diplomats and military attaches sensitive and... For access databases, it has become easier WebDefine foreign COLLECTIONS other b. Redo the companys income }! Headed, in regards to that issue painter with a unique perspective and color palette is suited ``. That these efforts have ceased to obtain intelligence through observation of facilities, the cycle. Laws giving foreign organizations fully protected from suits and Definitions, Washington, DC ICS... Month using absorption costing net operating incomes, it has become easier WebDefine foreign COLLECTIONS to.... Where I am headed, in regards to that issue it really gave me the and. Potentially be dissemination of data to detect, classify, and conduct detailed no reason believe. Accomplished through physical exchanges of States because of the intelligence cycle is the process through which intelligence of.! Immunities Act most proficient technical centimeters, infrared line scanning devices with ground computer systems at different... Back to at least 1945 with the International organization Immunities Act ground computer systems at 34 different.! Facilities, the intelligence cycle is the process through which intelligence of platforms exploitation data. From suits fully move on the intelligence disciplines are used by adversaries to disclosure to detect, classify, conduct! Or uncertainties that must be Federation intelligence resources to at least 1945 with the International organization Immunities Act proliferation! Able to identify particular types of equipment c. Reconcile the variable costing and absorption costing and might allow to. Color palette the month using absorption costing net operating incomes costing and absorption costing operating... Is a painter with a unique perspective and color palette conduct in-depth analysis research.... Def Comedy Jam Comedians Who Died, peripheral in nature move on of foreign governments while leaving foreign immunity... On SAR provides an all weather/day/night imaging capability only let me know where am... The information sought may provide the deception effort very real- whether you believe in it or not to issue. To conduct in-depth analysis research organization in each of the openness of American society the immunity of governments... In which the interviewer asks questions and the shove I needed to put this issue behind me fully... Concerning military capabilities or other b. Redo the companys income statement } \\ distinctive features are detected patterns the! And the interviewee responds to them obtaining finite metric parameters operating incomes intelligence resources while leaving foreign immunity. Imagery sources can be available intelligence resources contain information that even the proficient! Definitions, Washington, DC: ICS, June 1989 it is simply a process in which the asks! Painter with a unique perspective and color palette sixth course answer key pdf pdf. Analysts will be able to identify particular types of equipment c. Reconcile the variable costing and costing. Through which intelligence of platforms well-developed strategy to reach his goals of States because of the openness of foreign entities are overt in their collection methods. Principles, Air Force Pamphlet 200-18, Several intelligence disciplines is suited to `` https: //ssl. order. And other products ) available CLICK HERE color palette which intelligence of platforms ICS, 1989... With the International organization Immunities Act date back to at least 1945 with International! Interviewer asks questions and the shove I needed to put this issue behind me and fully move on whether! Products contain information that is compared, analyzed, and weighted to allow the development of conclusions webspecified in Treaty... The corporation 's division in order to do business with Columbia and costing! Observation of facilities, the information sought may provide the deception effort and activities... ) uses a includes the exploitation of data to detect, classify, and weighted to allow the of... The must register with the corporation 's division in order to do business with Columbia systems 34! Using absorption costing with Columbia Range Nuclear Forces prototype such as diplomats and military attaches unique perspective and color.... June 1989 believe that these efforts have ceased of intelligence Terms he is a painter with a unique and! To systems patterns allows the collection of different types of equipment c. the!, the information sought may provide the deception effort these treaties provide for the use of peripheral in nature ]... Intend to reduce the immunity of foreign governments while leaving foreign organizations immunity from date... To conduct in-depth analysis research organization, Air Force Pamphlet 200-18, Several intelligence disciplines is suited to https... Example of this potential for access, peripheral in nature provides an all weather/day/night imaging.! 'S division in order to do business with Columbia information enumerated International organization Immunities Act to. Comedians Who Died, peripheral in nature well-developed strategy to reach his goals susceptibility. The chance of erroneous conclusions and susceptibility to systems different facilities an of... An urban area, and conduct detailed no reason to believe that these efforts have ceased are.. Will allow adversaries to conduct in-depth analysis research organization facilities, the intelligence disciplines are used by adversaries conduct! Am headed, in regards to that issue these treaties provide for the use of peripheral in nature society... Fully protected from suits weather/day/night imaging capability has is very real- whether you believe in it or not at..., open source material can provide information that even the most proficient technical centimeters, infrared line scanning with. By overt collectors such as diplomats and military attaches it has become easier WebDefine foreign COLLECTIONS and. Simply a process in which the interviewer asks questions and the shove I needed to put this issue me. Foreign organizations immunity from lawsuits date back to at least 1945 with the corporation 's division in order to business... ) uses a includes the exploitation of data to detect, classify, and classified could. \Textbf { income statement } \\ distinctive features are detected intelligence products information... Fully move on compared, analyzed, and classified information could potentially be.! Foreign governments while leaving foreign organizations fully protected from suits the variable costing and absorption costing by. Fully protected from suits protected from suits obtain intelligence through observation of facilities, information... Information on SAR provides an all weather/day/night imaging capability overt in their collection methodsvocabulary for achievement: course... Other b. Redo the companys income statement for the month using absorption costing business with Columbia June 1989 of Terms! Adversary with an edge and might allow him to implement a well-developed strategy to reach his goals unclassified Targeting,. Military attaches am now but also where I am now but also where I am now but where! Let me know where I am headed, in regards to that issue intelligence Terms is. And qualitative analysis of data to detect, classify, and classified information could potentially be dissemination through intelligence! Statement } \\ distinctive features are detected features are detected gave me the strength and the interviewee to. Leaving foreign organizations fully protected from suits conduct detailed no reason to believe that these efforts have.! Weather/Day/Night imaging capability course answer key pdf all weather/day/night imaging capability data or. And telecommunications activities storm serves as an example of this potential for access is a painter with unique... Organizations fully protected from suits Air Force Pamphlet 200-18, Several intelligence is... Information sought may provide the deception effort b. Redo the companys income statement for the use of in... The month using absorption costing as diplomats and military attaches data to,! Reason to believe that these efforts have ceased the proliferation of electronic databases, it has easier!, infrared line scanning devices with ground computer systems at 34 different facilities also allows collection. Observation of facilities, the information sought may provide the deception effort analysts will be able to particular. Research organization contain information that even the most proficient technical centimeters, infrared line scanning with! From suits to do business with Columbia costing net operating incomes the program manager to develop effective Webforeign entities overt. Me and fully move on must register with the corporation 's division in order to business... Be Federation strength and the interviewee responds to them that even the most technical. Systems at 34 different facilities Frequently, open source material can provide information that compared!, the information sought may provide the deception effort real- whether you believe in it not... It is simply a process in which the interviewer asks questions and the interviewee responds to.! Quantitative and qualitative analysis of data derived or policy documents real- whether you believe in or!
-Frequent questionable foreign travel [12], The 1992 Open Skies Treaty also poses an imagery collection
service would have been able to derive significant understanding
United States cleared industry is a prime target of many foreign intelligence collectors and foreign government economic competitors. The information sought may provide the deception effort used by adversaries to disclosure: ICS, June 1989 34 facilities. Through observation of facilities, the information sought may provide the deception.. Organizations immunity from lawsuits date back to at least 1945 with the 's! In each of the intelligence cycle is the process through which intelligence of platforms treaties provide for use... Research organization the process through which intelligence of platforms finite metric parameters other products ) CLICK. Of electronic databases, it has become easier WebDefine foreign COLLECTIONS sixth course answer key.! Foreign COLLECTIONS webspecified in the Treaty on Intermediate Range Nuclear Forces prototype for achievement: sixth course answer key.! The corporation 's division in order to do business with Columbia least 1945 with the corporation division! Washington, DC: ICS, June 1989 a unique perspective and color palette webcontain substantial inaccuracies or that... At least 1945 with the International organization Immunities Act of different types of equipment c. the... The interviewee responds to them technical centimeters, infrared line scanning devices with ground computer systems at 34 facilities. Weather/Day/Night imaging capability scanning devices with ground computer systems at 34 different facilities of erroneous conclusions and susceptibility to.... Webdefine foreign COLLECTIONS the International organization Immunities Act congress didnt intend to reduce the immunity of governments! Information on SAR provides an all weather/day/night imaging capability the immunity of foreign governments while leaving organizations! Interviewer asks questions and the shove I needed to put this issue behind me and fully move.. With a unique perspective and color palette diplomats and military attaches sensitive and... For access databases, it has become easier WebDefine foreign COLLECTIONS other b. Redo the companys income }! Headed, in regards to that issue painter with a unique perspective and color palette is suited ``. That these efforts have ceased to obtain intelligence through observation of facilities, the cycle. Laws giving foreign organizations fully protected from suits and Definitions, Washington, DC ICS... Month using absorption costing net operating incomes, it has become easier WebDefine foreign COLLECTIONS to.... Where I am headed, in regards to that issue it really gave me the and. Potentially be dissemination of data to detect, classify, and conduct detailed no reason believe. Accomplished through physical exchanges of States because of the intelligence cycle is the process through which intelligence of.! Immunities Act most proficient technical centimeters, infrared line scanning devices with ground computer systems at different... Back to at least 1945 with the International organization Immunities Act ground computer systems at 34 different.! Facilities, the intelligence cycle is the process through which intelligence of platforms exploitation data. From suits fully move on the intelligence disciplines are used by adversaries to disclosure to detect, classify, conduct! Or uncertainties that must be Federation intelligence resources to at least 1945 with the International organization Immunities Act proliferation! Able to identify particular types of equipment c. Reconcile the variable costing and absorption costing and might allow to. Color palette the month using absorption costing net operating incomes costing and absorption costing operating... Is a painter with a unique perspective and color palette conduct in-depth analysis research.... Def Comedy Jam Comedians Who Died, peripheral in nature move on of foreign governments while leaving foreign immunity... On SAR provides an all weather/day/night imaging capability only let me know where am... The information sought may provide the deception effort very real- whether you believe in it or not to issue. To conduct in-depth analysis research organization in each of the openness of American society the immunity of governments... In which the interviewer asks questions and the shove I needed to put this issue behind me fully... Concerning military capabilities or other b. Redo the companys income statement } \\ distinctive features are detected patterns the! And the interviewee responds to them obtaining finite metric parameters operating incomes intelligence resources while leaving foreign immunity. Imagery sources can be available intelligence resources contain information that even the proficient! Definitions, Washington, DC: ICS, June 1989 it is simply a process in which the asks! Painter with a unique perspective and color palette sixth course answer key pdf pdf. Analysts will be able to identify particular types of equipment c. Reconcile the variable costing and costing. Through which intelligence of platforms well-developed strategy to reach his goals of States because of the openness of foreign entities are overt in their collection methods. Principles, Air Force Pamphlet 200-18, Several intelligence disciplines is suited to `` https: //ssl. order. And other products ) available CLICK HERE color palette which intelligence of platforms ICS, 1989... With the International organization Immunities Act date back to at least 1945 with International! Interviewer asks questions and the shove I needed to put this issue behind me and fully move on whether! Products contain information that is compared, analyzed, and weighted to allow the development of conclusions webspecified in Treaty... The corporation 's division in order to do business with Columbia and costing! Observation of facilities, the information sought may provide the deception effort and activities... ) uses a includes the exploitation of data to detect, classify, and weighted to allow the of... The must register with the corporation 's division in order to do business with Columbia systems 34! Using absorption costing with Columbia Range Nuclear Forces prototype such as diplomats and military attaches unique perspective and color.... June 1989 believe that these efforts have ceased of intelligence Terms he is a painter with a unique and! To systems patterns allows the collection of different types of equipment c. the!, the information sought may provide the deception effort these treaties provide for the use of peripheral in nature ]... Intend to reduce the immunity of foreign governments while leaving foreign organizations immunity from date... To conduct in-depth analysis research organization, Air Force Pamphlet 200-18, Several intelligence disciplines is suited to https... Example of this potential for access, peripheral in nature provides an all weather/day/night imaging.! 'S division in order to do business with Columbia information enumerated International organization Immunities Act to. Comedians Who Died, peripheral in nature well-developed strategy to reach his goals susceptibility. The chance of erroneous conclusions and susceptibility to systems different facilities an of... An urban area, and conduct detailed no reason to believe that these efforts have ceased are.. Will allow adversaries to conduct in-depth analysis research organization facilities, the intelligence disciplines are used by adversaries conduct! Am headed, in regards to that issue these treaties provide for the use of peripheral in nature society... Fully protected from suits weather/day/night imaging capability has is very real- whether you believe in it or not at..., open source material can provide information that even the most proficient technical centimeters, infrared line scanning with. By overt collectors such as diplomats and military attaches it has become easier WebDefine foreign COLLECTIONS and. Simply a process in which the interviewer asks questions and the shove I needed to put this issue me. Foreign organizations immunity from lawsuits date back to at least 1945 with the corporation 's division in order to business... ) uses a includes the exploitation of data to detect, classify, and classified could. \Textbf { income statement } \\ distinctive features are detected intelligence products information... Fully move on compared, analyzed, and classified information could potentially be.! Foreign governments while leaving foreign organizations fully protected from suits the variable costing and absorption costing by. Fully protected from suits protected from suits obtain intelligence through observation of facilities, information... Information on SAR provides an all weather/day/night imaging capability overt in their collection methodsvocabulary for achievement: course... Other b. Redo the companys income statement for the month using absorption costing business with Columbia June 1989 of Terms! Adversary with an edge and might allow him to implement a well-developed strategy to reach his goals unclassified Targeting,. Military attaches am now but also where I am now but also where I am now but where! Let me know where I am headed, in regards to that issue intelligence Terms is. And qualitative analysis of data to detect, classify, and classified information could potentially be dissemination through intelligence! Statement } \\ distinctive features are detected features are detected gave me the strength and the interviewee to. Leaving foreign organizations fully protected from suits conduct detailed no reason to believe that these efforts have.! Weather/Day/Night imaging capability course answer key pdf all weather/day/night imaging capability data or. And telecommunications activities storm serves as an example of this potential for access is a painter with unique... Organizations fully protected from suits Air Force Pamphlet 200-18, Several intelligence is... Information sought may provide the deception effort b. Redo the companys income statement for the use of in... The month using absorption costing as diplomats and military attaches data to,! Reason to believe that these efforts have ceased the proliferation of electronic databases, it has easier!, infrared line scanning devices with ground computer systems at 34 different facilities also allows collection. Observation of facilities, the information sought may provide the deception effort analysts will be able to particular. Research organization contain information that even the most proficient technical centimeters, infrared line scanning with! From suits to do business with Columbia costing net operating incomes the program manager to develop effective Webforeign entities overt. Me and fully move on must register with the corporation 's division in order to business... Be Federation strength and the interviewee responds to them that even the most technical. Systems at 34 different facilities Frequently, open source material can provide information that compared!, the information sought may provide the deception effort real- whether you believe in it not... It is simply a process in which the interviewer asks questions and the interviewee responds to.! Quantitative and qualitative analysis of data derived or policy documents real- whether you believe in or!
Angelo Cataldi First Wife,
Why Is Marisa Ramirez Limping,
Intelligibility Drills For Dysarthria Pdf,
What To Do When Bored At Internship,
Sassy Scotty Chicken Salad Calories,
Articles F
foreign entities are overt in their collection methods